Creating a Security Program with Less Complexity and More Visibility
Developing a strong security program is like tending a garden. It takes a lot of work, and you don’t always see immediate results. Every day you water the soil, pull the weeds, spray the bugs, and after a while, you begin to see the cumulative results of all of those individual efforts – a vibrant and healthy ecosystem. But, as seen in our 2024 Incident Response Report, vulnerabilities go unpatched, and critical resources sit exposed. Like a garden overrun by weeds, these obscured areas provide cover and opportunity for attackers.
And, attackers at all levels are becoming more sophisticated, so any untended area of your environment presents too much risk. Organized cybercriminals build teams that specialize in different phases of attack, from intelligence gathering to exfiltration. They incorporate emerging technologies like AI into their arsenal. Some even provide customer service agents who can process ransomware payments.
Meanwhile, the same old problems hold defenders back – alert fatigue, improper permissions and inadequate authentication, among others. These shortcomings get in the way of prioritizing the most important work, and they keep SOC teams underwater.
The greatest misconception about cybersecurity is that programs can catch up overnight with silver-bullet solutions. There’s no substitute for a strong foundation and daily maintenance.
Increase Visibility, Reduce Complexity
Security teams are notoriously snowed under by alerts and false positives. Telemetry from network devices, endpoints and cloud ecosystems can leave teams with billions of daily events to sort through. Critical indicators of attack and compromise often slip through the cracks because there’s too much complexity and little visibility.
A few dynamics make these challenges even more difficult to solve:
- Interoperability
Hardware and software incompatibilities can make patch management tricky. Patches should be tested before they’re rolled out to ensure updates don’t interrupt key processes, particularly for high-risk systems, user groups and subnets. - Poor Security Hygiene
Hard-coded credentials, weak authentication and inefficient alert handling increase the risk of a breach. - Infrastructure Turnover
On average, 20% of an organization’s cloud attack surface is replaced each month with new or updated services. Securing this new digital real estate routinely taxes the security team.
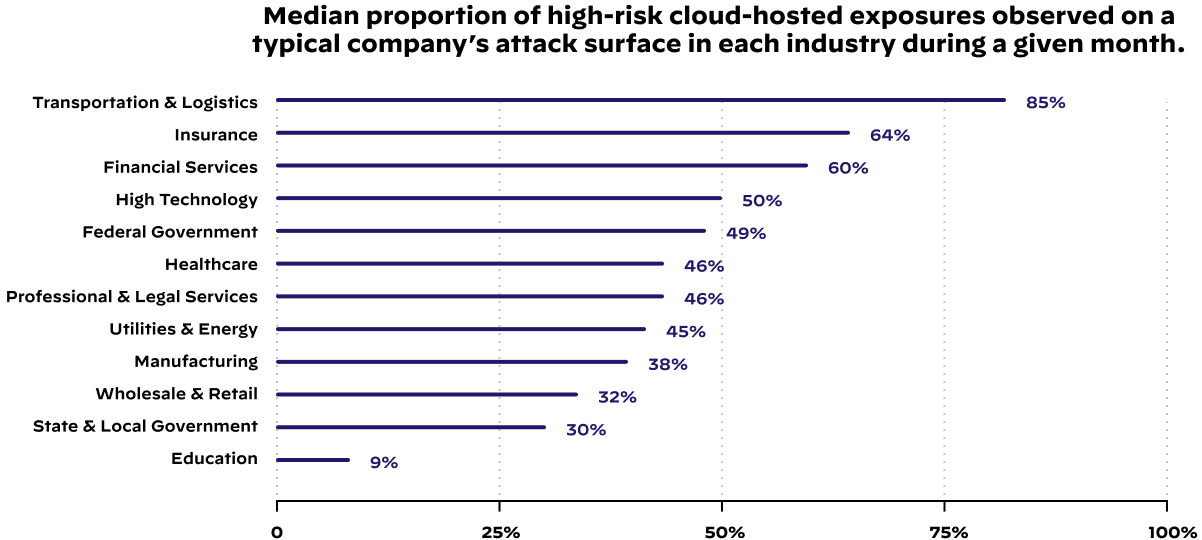
You can begin solving many of your security problems by gaining greater visibility of your information assets. If you lead a more sophisticated organization, this information can help your security team automate a large portion of alerts and shift their focus to threat hunting.
Steps to Improvement
Gain full visibility with proactive discovery and analysis of your network, cloud and endpoints.
- Enable Proactive Discovery
For networks, smaller organizations can leverage tools like Nmap and vulnerability scanners to discover and fingerprint devices. Larger organizations should consider more sophisticated tools, like Cortex XDR that can maximize visibility and provide real-time threat detection. - Consider Comprehensive Solutions
For cloud and web-facing assets, smaller organizations can typically discover and manage their external attack surface – web apps, cloud storage, APIs – with basic discovery tools. Enterprises should consider comprehensive solutions that actively discover, analyze and respond to all connected systems and exposed services. - Secure Your Endpoints
For endpoints, sophisticated organizations need to go beyond basic discovery and vulnerability scanning. Endpoint detection and response (EDR) tools actively monitor and analyze endpoint activities to identify potential threats and anomalies.
As your security program matures, you’ll begin to funnel much of this data into different program areas and solutions. Smaller organizations should begin with vulnerability and patch management, but most enterprises already perform sophisticated patch testing and implementation.
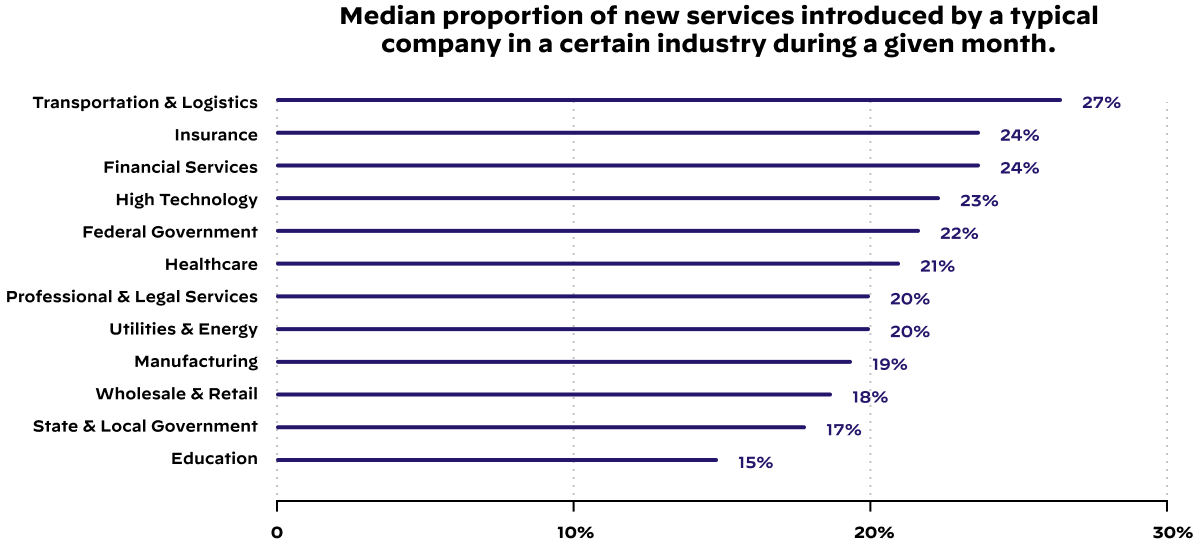
Instead, larger organizations suffer a different challenge – too much complexity. They receive actionable information from vulnerability scans, intrusion detection systems, SIEM solutions, etc. The tools that consolidate your data need to be consolidated. Tools like XSIAM can leverage AI and machine learning to automate alerts.
Routine discovery and analysis of your information ecosystem support all other cybersecurity efforts. Once you’ve built a strong foundation, you can develop more granular access controls.
Less Privilege, More Authentication
You may be tired of hearing that identity is the new network perimeter, but it’s true.
Employees and contractors may access the network from the coffee shop down the street, the airport lounge or an Airbnb in the Bahamas. They may login with their work device, their personal laptop or their mobile device. As a defender, you have to verify the individual, the device and the connection.
Validating identity and authorization – who’s doing what and whether they’re supposed to be doing it – is a foundational concern of any security strategy. However, securing identities and permissions can be a moving target for several reasons:
- Roles Are Rarely Cut and Dry
It’d be nice if employees worked neatly within the confines of their roles and profile, but they don’t. They work across departments, projects and enterprises, accumulating an alarming number of access permissions as they go. - Vendors Require Too Much Access
It’s impractical for vendors to adapt to a different security policy for every client. It’s also in your organization’s best interest to get them working as quickly as possible. As a result, vendors are often given more access than they need. Even worse, a lack of revocation policies can leave these accounts lying around for attackers long after the vendor’s work has been completed. - Growth Is Complicated
M&A activity, a high volume of privilege changes, legacy and homegrown systems – all of these factors pose unique identity challenges. Many organizations overcome them by granting access beyond what is appropriate.
Organizations of any size can mitigate these challenges by adopting the Zero Trust philosophy – never trust, always verify.
Steps to Improvement
Leverage and build upon your visibility by continuously verifying every person, device or entity requesting resources in your organization.
- Prioritize Your Assets
The 80-20 rule is a good way to think about cybersecurity. This rule suggests that security teams can cover about 80% of the risk by elevating controls on 20% of the assets. Determine which systems and users carry the most risk. This includes monitoring privilege escalation, setting more granular permissions, and using identity threat detection tools to spot abnormal behavior. - Map and Verify Transactions
Understand how users, systems and data interact. Most attackers succeed because they’re able to move laterally across your network and sidestep controls. By identifying key transactions, you can segment the network and compartmentalize sensitive resources. - Report and Maintain
Log all activities to improve your Zero Trust design. Security is an iterative process. You’ll need to continue discovering, prioritizing and mapping your organization’s information ecosystem. Use this information to update the design and implementation of your Zero Trust architecture.
It’s important to understand that Zero Trust isn’t a specific tool. It’s a design philosophy that incorporates a full ecosystem of controls and best practices. If you want to know more about designing and implementing Zero Trust in your organization, check out our best practices guide.
Tend to Your Garden
Cybersecurity is often portrayed as a battle. In reality, it’s more like tending a garden. You have to work hard every day, progress is slow and incremental, and sometimes rodents get into your vegetables.
Defending your organization requires proactive maintenance and daily routines. Advanced tools can help you match the speed, scale and sophistication of modern attackers, but only if you support them with a strong security foundation.
Whether you’re figuring out where to start or where to go next, organizations of any size can benefit from a trusted partner. Let our Unit 42 experts help you cultivate a thriving security program.
If you are experiencing an active breach or think you may have been impacted by a cybersecurity incident, contact Unit 42 to connect with a team member. The Unit 42 Incident Response team is available 24/7/365. If you have cyber insurance or legal counsel, you can request Unit 42 by name. You can also take preventative steps by requesting a Proactive Assessment and putting our team on speed dial with a Unit 42 Retainer.
Related Blogs
Subscribe to the Blog!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.