SmartGrouping - Precision AI™-Driven Investigation
SmartGrouping is a crucial aspect of security operations, allowing to connect disparate alerts and paint a comprehensive picture of an attack. It's like piecing together a puzzle, where each alert represents a piece, and the complete picture reveals the attacker's intent, methodology and scope of impact.
In the past, analysts would have gone through all of these pieces by themselves, investigating each individual alert coming from different sources, hunting down for more clues, getting more information from the environment and eventually trying to draw the attack story.
With Cortex capabilities, the story is different. Imagine this: your security system throws up a flurry of alerts coming from different sources and used with different techniques—a suspicious login attempt, credential theft, unusual data exfiltration, and a sudden spike in outbound network traffic. Individually, these might seem like isolated alerts. But with SmartGrouping, correlating these seemingly unrelated alerts reveals a coordinated attack unfolding in near real-time.
This grouping offers several benefits:
- Reduced noise: By grouping related alerts, analysts can focus on the bigger picture, leading to faster incident resolution.
- Faster investigation: Instead of investigating each alert individually, analysts can delve into the grouped incident, saving valuable time and resources.
- Improved context: it provides a comprehensive view of the attack, enabling analysts to understand the attacker's motivations, tactics, and potential impact.
- Align the analysts’ ground truth: In the past, analysts used their own methods to connect the dots. With this mechanism, we align the investigation baseline to start with, ensuring everyone uses the same knowledge all across the teams.
- Actionable insights: By understanding the full scope of the attack, analysts can prioritize response efforts and take targeted actions to mitigate the damage and prevent future attacks.
Ultimately, SOC teams can respond more effectively to cyberthreats with help from SmartGrouping.
SmartGrouping Analytics: Finding the Hidden Links
Imagine you are trying to solve a mystery in limited time. You have a box full of clues: some big, some small, some seemingly unrelated. You could be the detective, spending time sorting through those clues and connecting the dots to reveal the full picture, or you can get help from SmartGrouping. It uses smart statistical algorithms along with security context to find the most relevant pieces of information and build a clear attack story.
By filtering out the noise and focusing on the right information, SmartGrouping encapsulates what happened, who might be involved, and what the potential impact that could be. This allows security teams to take better decisions, prioritize threats, and ultimately stop threats in their tracks.
SmartGrouping in Analytics Framework
The analytics framework is a centralized system used to run advanced algorithms and analytical logics across the different products and data sources to provide enhanced detection, grouping and prioritization flows. This system can profile entities and behaviors to precisely determine which entities are related or unrelated to an attack and only include related ones in the attack story.
For example, imagine you have an alert with a popular domain and want to decide if this domain is part of the attack. With analytics, we can determine the reputation of this domain and use this information to decide if we want to keep this entity as part of our grouping logic or entirely ignore this entity to reduce irrelevant links.
Artifacts Explained
When an alert is triggered, the system, along with its powerful analytics capabilities, digs into the alert’s details to uncover the story behind the attack. Think about a list of entities, carefully selected by the system, pointing to the most relevant information about the alert and its relevant events. Each entity can be a simple one, like hash, or a complex representation, like the behavior of an identity. Not every extracted entity is used for grouping, as it depends on its effectiveness and relevance, and could be used only for presentation and enrichment.
These important entities are also known as "artifacts". They can be either presented in the incident level in the UI as enrichment indicators and/or can be used for grouping based on a logical order per their specificity.
Think of them like in a forensic investigation, starting with the most precise details at the top, and gradually expanding the investigation with broader entities at the bottom. For instance, at the top, you might find a specific causality process which is unique to the attack process on the infected machine, while moving to the bottom, you could find the identity of the involved user spreading to other machines.
This order ensures that the system smartly focuses on the most specific artifacts first. If a specific artifact is found, it helps to narrow down the scope of the attack quickly. If no specific artifacts were found, the system diligently moves on to the broader artifacts, widening the search to find connections and piece together alerts which would have gone unnoticed otherwise. To ensure we don’t add up unrelated alerts, artifacts might be set with time-to-live (TTL) in order to make sure we only add them up at the relevant time-frame of the attack to avoid mixing them with unrelated alerts.
SmartGrouping & SmartScore for Quicker Triage
As mentioned above, SmartGrouping helps paint a clearer and full context picture of the attack story. This richer understanding empowers SOC teams to prioritize and investigate threats more effectively.
SmartScore, a system that predicts the maliciousness of an incident, further leverages the power of SmartGrouping. It does that by utilizing this rich context to extract features from the grouped incidents and their associated alerts, and assigns a score indicating the likelihood of malicious intent. The score serves as a valuable guide for analysts, helping them focus on the most critical incidents and prioritize their response efforts.
Over time, the system keeps getting updated with new periodic logics and artifacts. This enhancement adds more context in, enabling customers to better understand the attack flow while also adding more context for SmartScore to better infer its results.
By combining SmartGrouping and SmartScore, security teams can achieve a more efficient and accurate triaging process, respond swiftly, and effectively while minimizing the impact of attacks.
SmartGrouping Explainability
We are at a point where we want to better understand what is behind our incident and how and why it was grouped. Let’s assume we found an incident that was triggered by a ransomware variant which involved various prevention and analytics alerts. Let’s look deeper into the analysis flow.
Ransomware Protection Incident
1. This example starts with an incident number 35629:
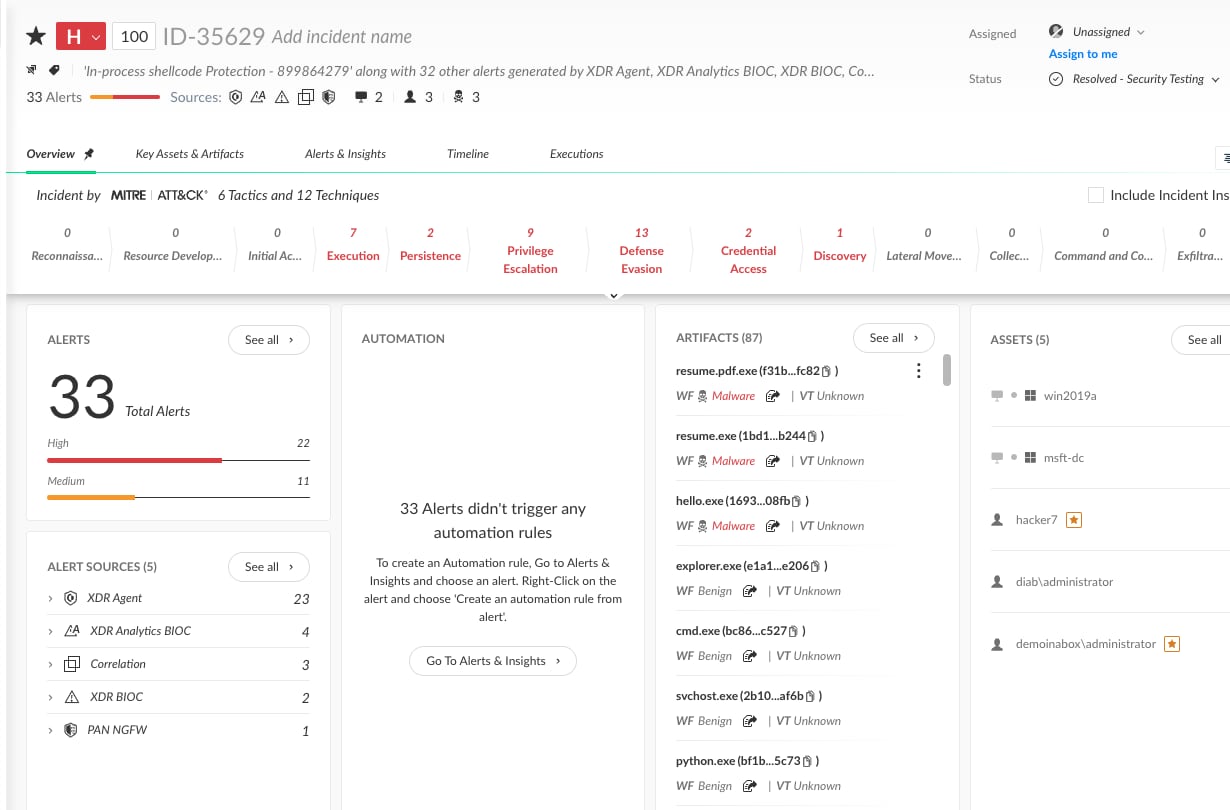
2. As can be seen, the artifacts portion on the right side was filled with many entities, including files, processes, users, and hosts.
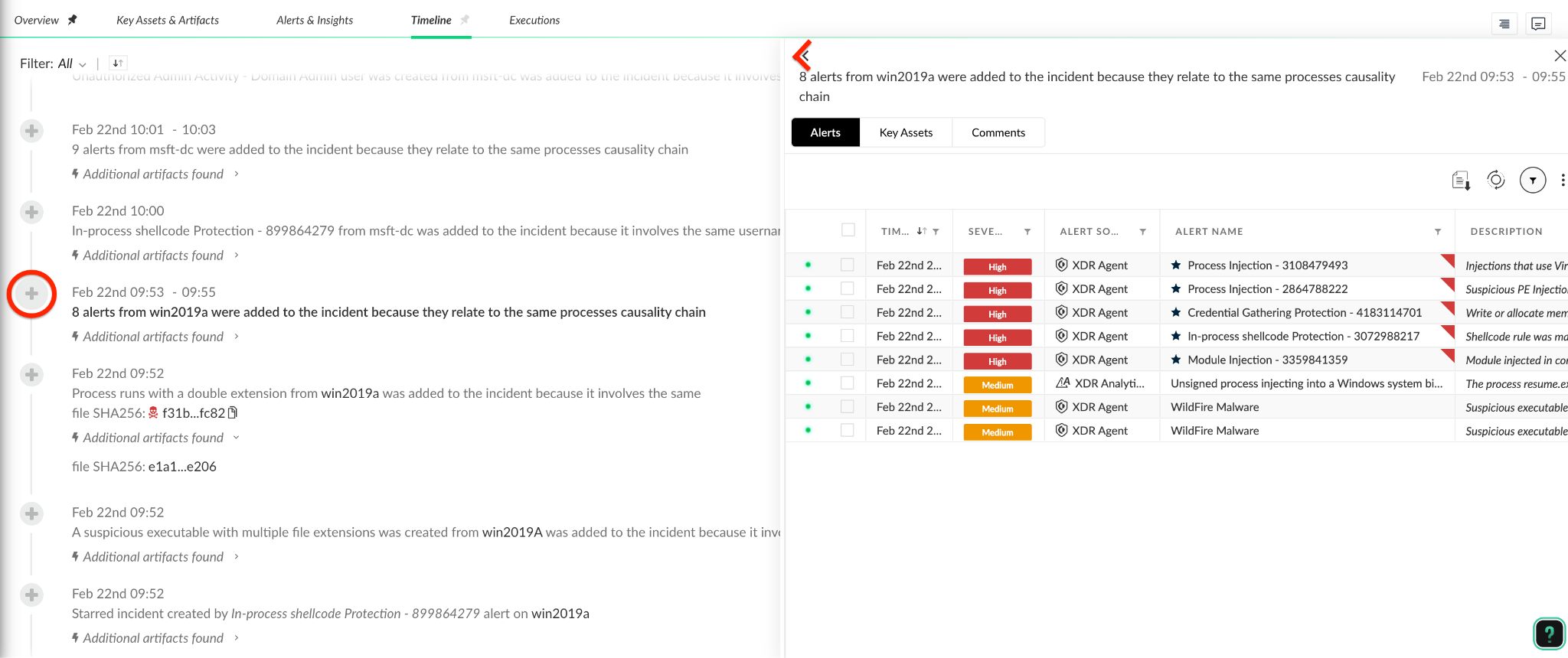
3. In order to understand what artifact was involved in our SmartGrouping decision, we first go to the timeline tab to get further information:
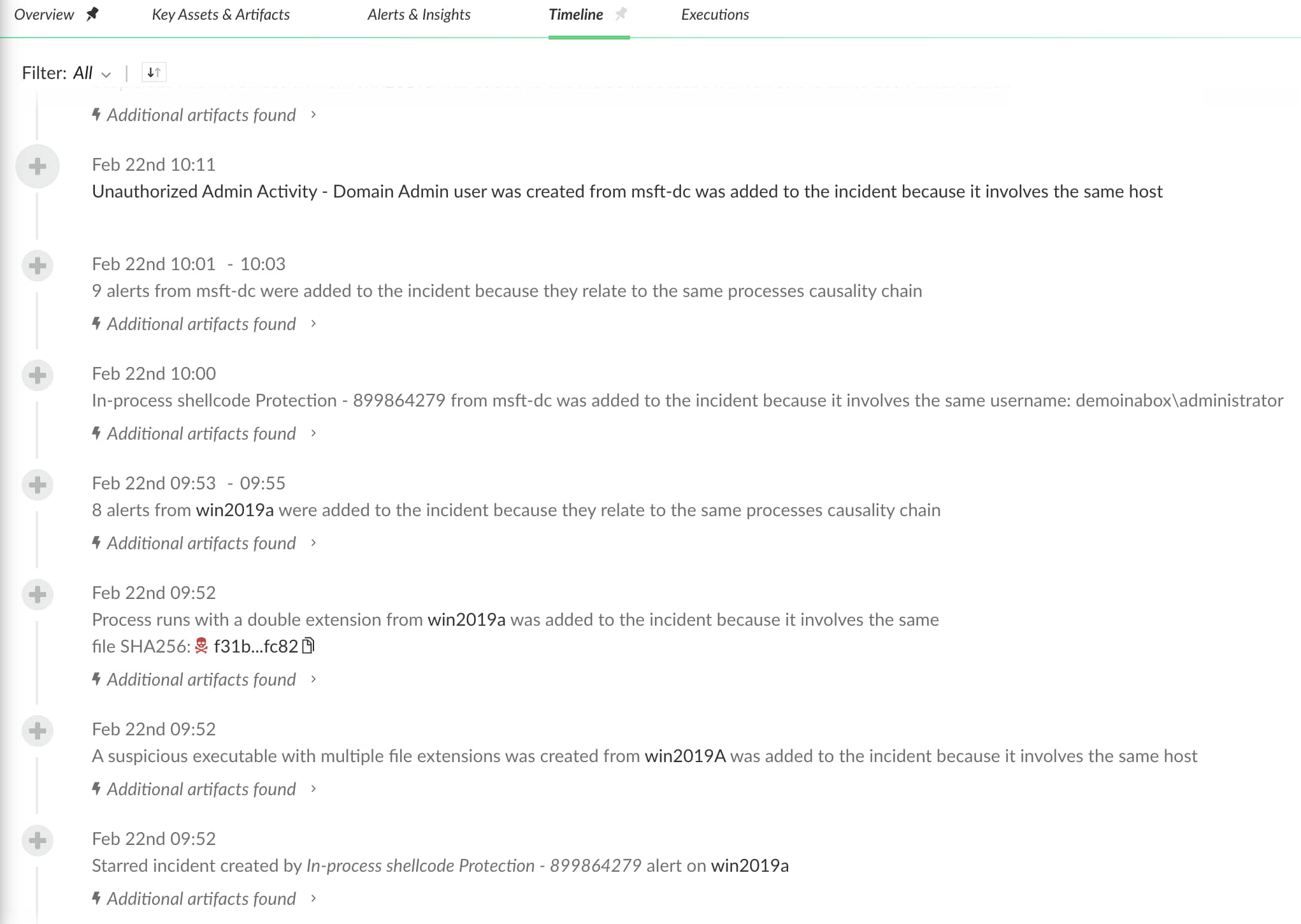
4. The timeline tells us that the first generated alert is “In-process shellcode”. This alert extracted various artifacts, including the host artifact “win2019a”. Once extracted, the next alert “a suspicious executable with multiple extensions” included the same host artifact which was used to link them together into the same incident.
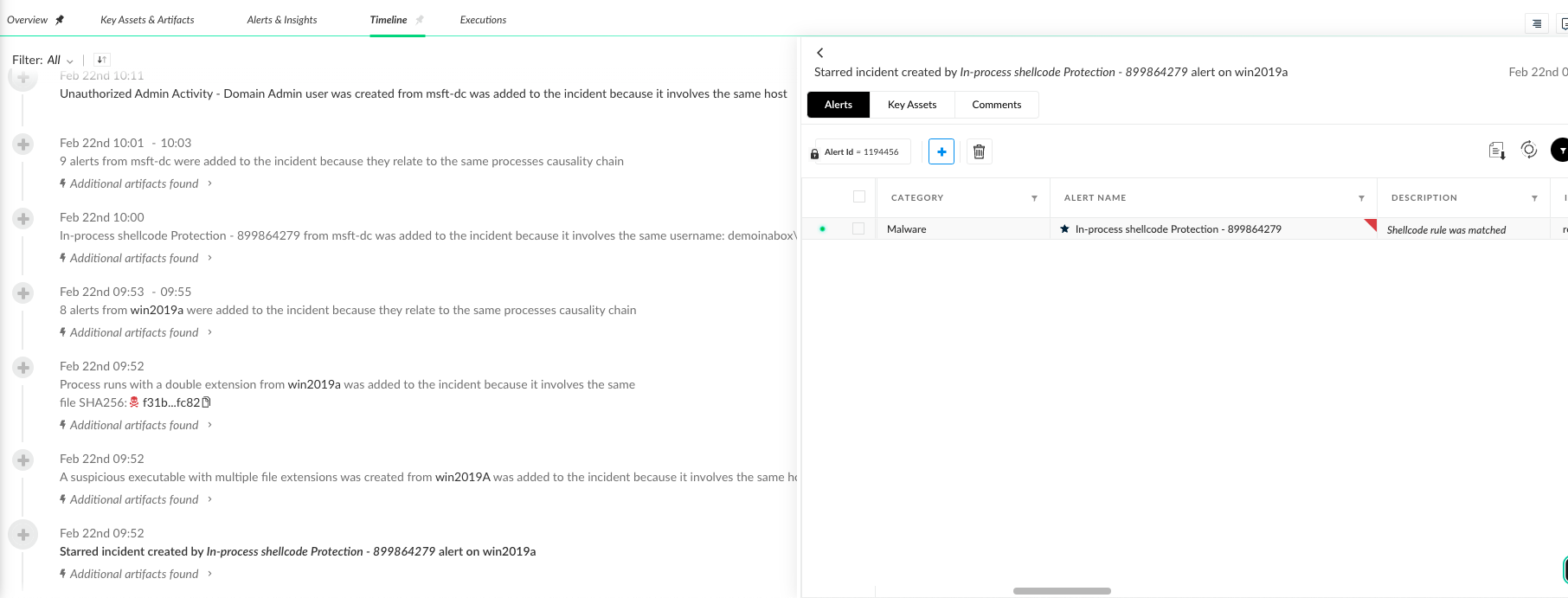
5. Each alert yields its own related artifacts which can pull more alerts and cause a chain effect that leads to more alerts being grouped together. For example, if we go upper in the timeline, we can see other alerts that were linked by file, causality artifacts, or a user asset.
In this case, the user entity is a great example of the analytics power. The analytics logic does not only extract the user involved in the attack story but also ensures that it reveals an actual effective user.
6. If you want to dive into the alerts in each artifact, clicking on the relevant grouping part will unfold all the related alerts that were joined and were linked by the same one.
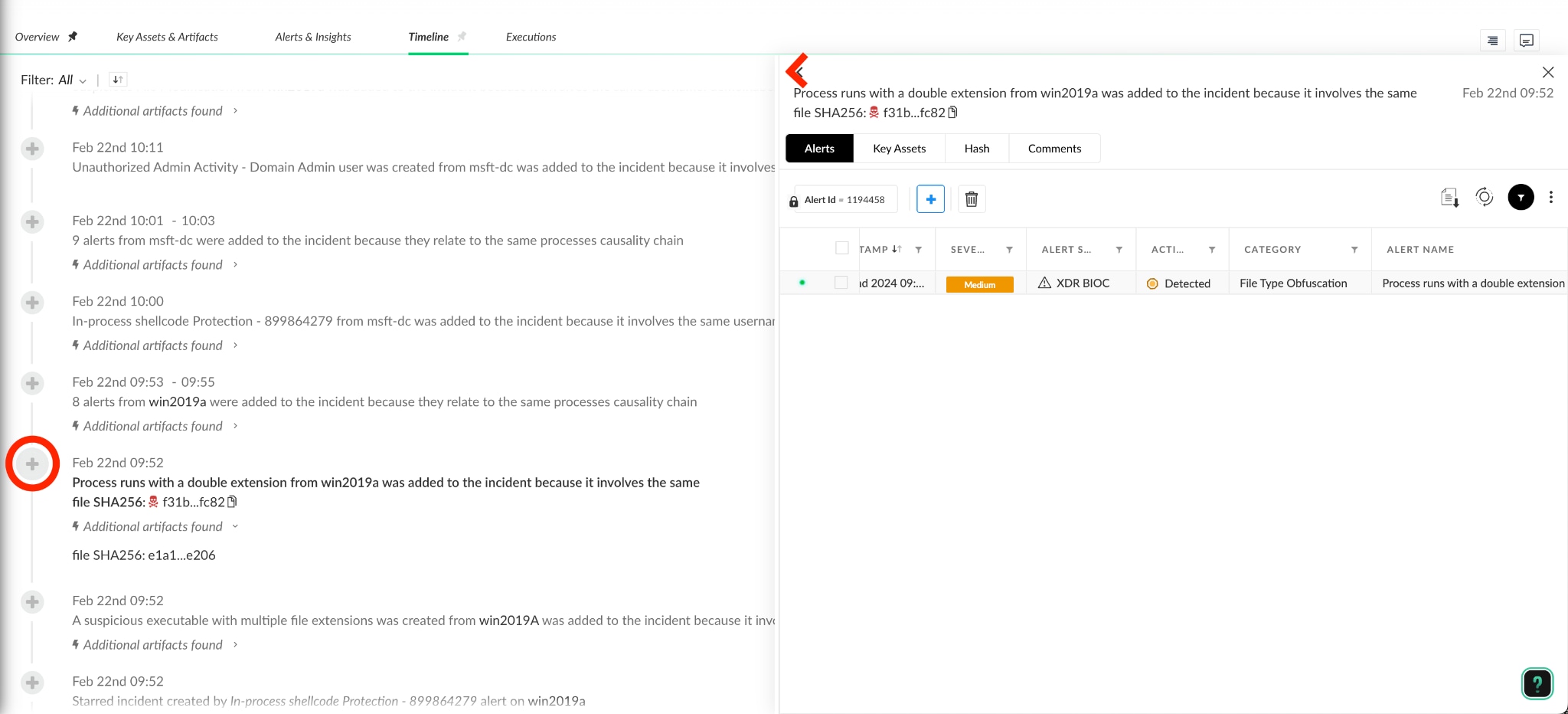
From this point, you have gathered all the knowledge and tools you need to keep going with the investigation and, if needed, take further actions.
Frequently Asked Questions
SmartGrouping vs. Stitching: Is It the Same?
These terms are different and sometimes tend to be confused. Let’s try to clear out the terminology.
To provide a complete and comprehensive picture of the events and activity surrounding an event, Cortex XDR/XSIAM correlates together firewall network logs, endpoint raw data, and cloud data across your detection sensors. The act of correlating logs from different sources is referred to as log stitching and helps you identify the source and destination of security processes and connections made over the network.
This stitching logic is unrelated to grouping directly and is focused on how we can enrich and enhance the event data from all data sources to enable better visibility. For example, when a connection is seen through the firewall and the endpoint, the endpoint can provide information on the processes involved and the chain of execution while the firewall can provide information on the amount of data transferred over the connection and the different app IDs involved.
SmartGrouping leverages this rich stitched data to extract more artifacts and improve grouping. For example, if a FW alert was stitched with a process information, we can then leverage this process information to extract more artifacts and, with that, link more alerts that contain similar process information into the same incident.
How Does SmartGrouping Work on Low Severity Alerts?
While in most cases we group medium or higher severity alerts, in some cases like in identity/cloud/SaaS areas, we allow grouping of low severity alerts. This is because these areas often generate many alerts that, while individually insignificant, can provide valuable insights when grouped together. Also the majority of these alerts tend to fall into the low alerts bucket due to their volume and their nature, which makes it even more crucial to leverage them all together.
For example, think about a series of low-severity login attempts from unusual locations might point to reconnaissance activity or a potential attack. By grouping these alerts, analysts can quickly identify suspicious patterns.
You might ask yourself where do all the other low severity alerts flow in?
- All the alerts arrive at the alerts table and can be either searched and consumed from there or using the Cortex platform API.
- In EDR related areas, customers can use the insights tab to connect the current incident with other low/info severity alerts
It is worth mentioning that we reserve the right to change and update the logic per need to make the story aligned on what’s crucial based on data source and type.
What is the Specific Logic Behind Artifact and Artifact Selection?
Each artifact has its own secret sauce logic and is kept as the company IP. This logic can also be updated and tuned on a regular basis. Sharing how one artifact works today will not guarantee that it will work the same tomorrow. With that in mind, the general description for each artifact is provided within the timeline tab.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.