Barracuda Networks Has a Predator that Can’t be Patched
On May 19, network security vendor Barracuda Networks identified a vulnerability (CVE-2023-2868) in their email security gateway (ESG) device and on May 20, pushed patches to the flaw for all affected appliances. In its advisory, Barracuda said the vulnerability existed in the software component that scans email attachments for malware. More alarmingly, the devices appear to have been exploited as early as October 2022 with a malware strain granting persistent backdoor access.
In an unexpected turn of events, on June 6, Barracuda began urging customers to fully decommission and replace affected ESG devices. “Impacted ESG appliances must be immediately replaced regardless of patch version level,” the company’s advisory warned. “Barracuda’s recommendation at this time is full replacement of the impacted ESG.”
Barracuda’s guidance to replace devices, not just patch them, caught the attention of security professionals worldwide: “I can only remember a handful of times where the fix was just to replace it,’” said Chris Tillett, senior engineer at Palo Alto Networks, who has been in the industry for 30 years. “It is very rare that a company can’t patch a vulnerability and recommends replacing it with a new device,” added Ali Islam, director of engineering at Palo Alto Networks.
If an attacker gains access to an exposed ESG, they can potentially intercept, read, and modify emails, bypass security filters, inject malware or phishing links, steal sensitive data, disrupt email services, and compromise the organization’s overall email security and communication integrity. The ramifications of such an attack are endless and you will want to investigate immediately. An attack surface management tool can help.
Cortex Xpanse helps respond to zero day vulnerabilities through continuous monitoring and alerting of exposures that allow an organization to quickly react to discovered threats and proactively manage risk. In the case of ESG devices, Xpanse can identify a device that is deployed as a physical or virtual appliance, or in a public cloud environment like AWS or Microsoft Azure, and attribute with high confidence if that device belongs to an organization or one of its global subsidiaries.
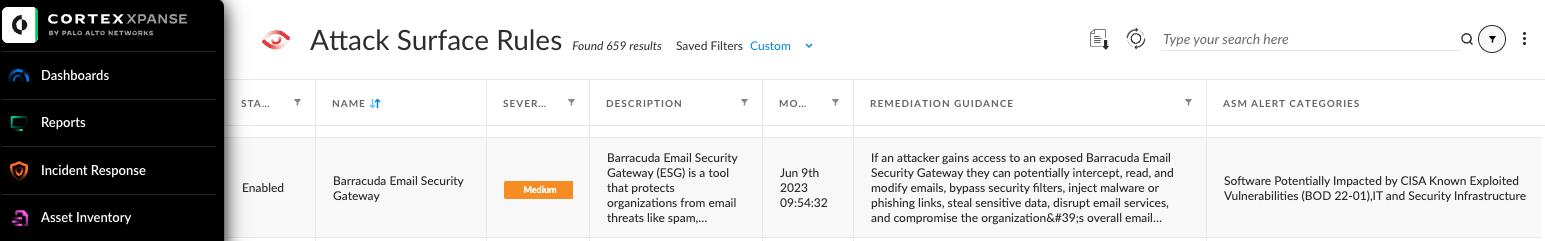
SOC teams spend considerable time and money researching and responding to global threat events and zero-day exploits. The Threat Response Center in Expander simplifies and streamlines your response to vulnerabilities like this one by aggregating the most important information about the threat and its impact on your organization in one place.
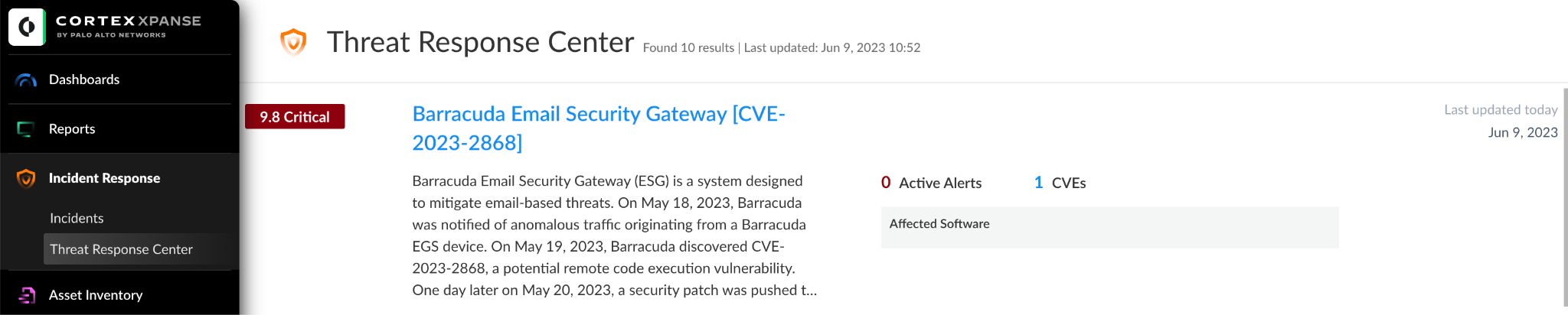
Xpanse identified the Barracuda ESG threat event as a critical and high-risk vulnerability that allows threat actors direct access to assets, leading to widespread impact across corporate networks. Devices and applications impacted by such vulnerabilities are at risk of exploitation remotely over the public-facing internet. These threats often allow threat actors to gain remote control of systems. In the Threat Response Center, analysts can access alerts, incident reports, mitigation guidance, and more to triage their incident response workflow.
By providing actionable context, like asset and service owners, Xpanse ensures accountability and provides an automated response to deploy missing agents and scan unmanaged assets. Given the severity of this vulnerability, it is crucial for organizations to address this issue promptly to prevent potential breaches.
Check out A Day in the Life of a Vulnerability Analyst to learn more about Cortex Xpanse.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.