As companies embrace the new reality of remote and hybrid work, organizations need a plan to secure remote employees for the long term, starting with the networks they are on.
The global pandemic resulted in a mass exodus of employees away from the relative safety of corporate networks. Seemingly overnight, operations were migrated—some of them business critical—to home networks on multiple devices with little time to plan and execute security processes. Even now, remote workers are staying remote, but moving around and adding public networks to worry about, like cafes, hotels, etc.
This all puts large amounts of stress on corporate cybersecurity teams, protocols and systems, and it exposes technology gaps between corporate locations and remote home offices, especially in terms of the limited visibility into the security of the remote networks employees are on.
Remote Protocols and Networks are Insecure
With employees, partners, and vendors working remotely, organizations face a greater risk to internal systems and data being exposed and attacked. This could be due to the increased usage of Remote Desktop Protocol (RDP) to support remote workers, employees using insecure networks, or increased usage of VPNs.
RDP routinely ranks as the number one security issue across the global attack surface, according to Cortex Xpanse data, and Unit 42 research found RDP to be the initial attack vector in half of all ransomware attacks. Consumer-grade networking hardware has also become the focus of cyberattackers, exposing more and more vulnerabilities putting remote employees at risk.
Additionally, while VPNs provide encryption, device security, and online privacy, concerns over their inherent security existed before COVID-19 making the huge bump in usage all the more worrisome.
The Cybersecurity and Infrastructure Security Agency (CISA), which is a part of Department of Homeland Security (DHS), issued an alert pointing to specific work-from-home vulnerabilities and potential VPN attacks, encouraging users to implement multifactor authentication (MFA) and stronger password usage.
In CISA’s alert, they offered the following considerations for teleworkers:
- As organizations use VPNs for telework, more vulnerabilities are being found and targeted in VPN software by malicious cyber actors.
- As VPNs are 24/7, organizations are less likely to keep them updated with the latest security updates and patches.
- Malicious threat actors may increase phishing emails targeting teleworkers to steal their usernames and passwords.
- Organizations that do not use MFA for remote access are more susceptible to phishing attacks.
- Organizations may have a limited number of VPN connections, after which point no other employee can telework. With decreased availability, critical business operations may suffer, including IT security personnel’s ability to perform cybersecurity tasks.
To help reduce exposure and compromises, incorporating security best practices are critical. This includes:
- Ensuring that insecure network configurations aren’t exposing risky services on corporate devices.
- Gaining visibility to dynamically change policies and alter access controls based on employee location.
- Identifying endpoints connecting through known vulnerable routers and assessing the need to deploy enterprise-grade hardware to key employees.
- Measuring the organizational risk associated with key employees working from home or temporary networks.
Secure Your Remote Employee’s Attack Surface
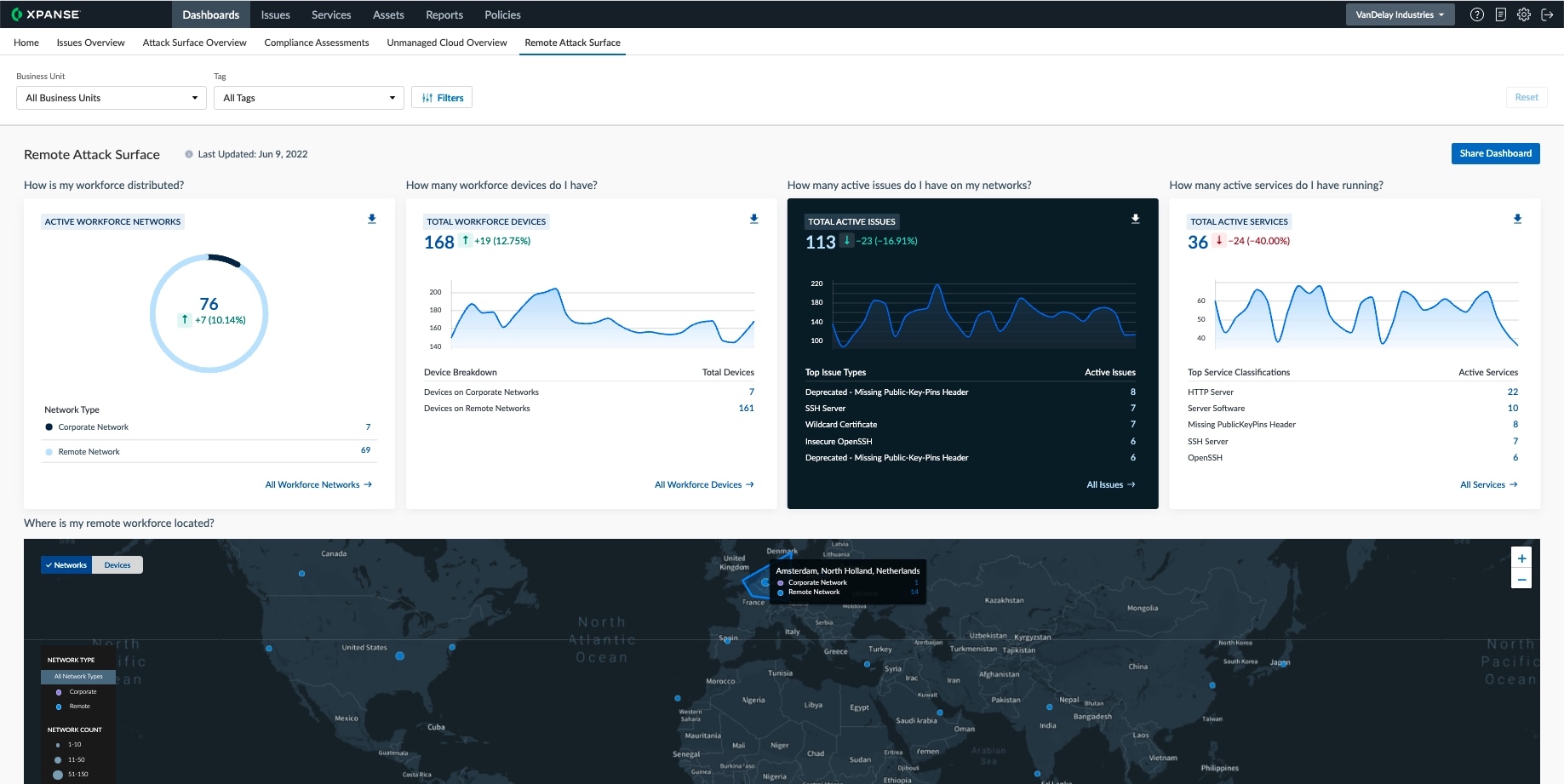
Fig 1: Overview of your remote networks and vulnerabilities
ASM for Remote Workers is an API integration between Cortex® Xpanse™ and both Cortex XDR and Prisma® Access with GlobalProtect™ agents. It allows organizations to effectively identify and get alerts on security issues on remote worker systems and network environments using public asset information discovered by Xpanse. Some of the benefits include the ability to:
- Identify risks for key remote employees and deploy enterprise-grade hardware selectively.
- Use visibility to dynamically change policies and alter access controls based on employee location.
- Improve mean time to respond (MTTR) by providing additional network data to a given incident.
- Find the internal and external IP mapping of your remote workforce.
- Discover the gaps in coverage of Cortex XDR agents in your organization.
- Ensure employees are using an approved VPN service.
- Improve MTTR by providing additional network data to a given incident identified by Cortex XDR.
- Identify employees working from unapproved locations and employees not using VPNs.
How It Works
Xpanse + Cortex XDR
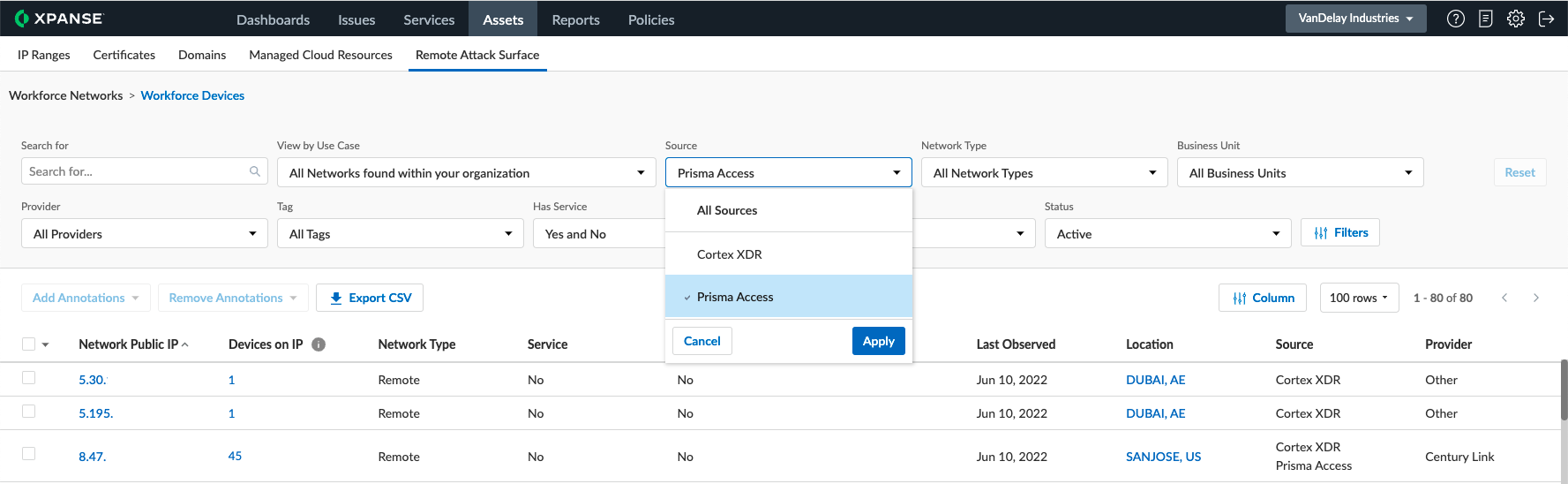
Fig 2: Leverage either Cortex XDR or Prisma Access with Cortex Xpanse to protect your remote workers
The integration gathers endpoint data from Cortex XDR (only assets that have a public IP address and have been seen in the last 24 hours) to identify remote workforce devices associated with your organization. It then combines this data with Xpanse’s global scan data to identify risky issues and services running on the networks where your employees are located, giving you a complete picture of your remote workforce.
Cortex XDR® gives you internal insight into what’s running on those devices, while Xpanse gives you the external perspective and identifies what’s exposed to the internet. Teams can remediate risky issues identified on remote networks—either directly on the device via Cortex XDR or via network configurations.
Xpanse + Prisma Access and GlobalProtect
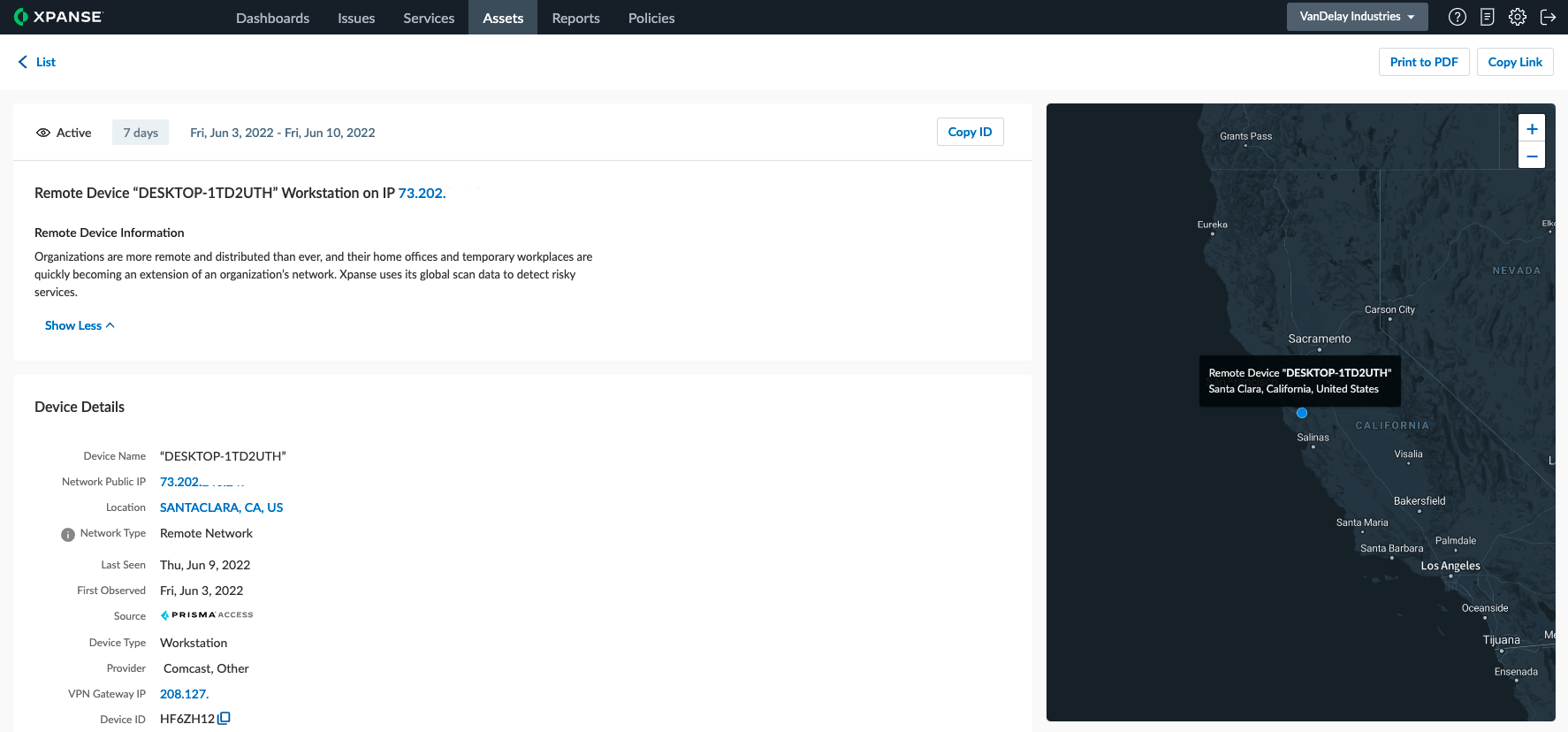
Fig 3: Get granular visibility into your remote worker exposures
The integration gathers GlobalProtect VPN client data/device data, which could come either through a Prisma Access deployment using GlobalProtect or from a GlobalProtect instance installed on an NGFW (only assets that have a public IP address and have been seen in the last 24 hours) to identify remote workforce devices associated with your organization. It then combines this data with Xpanse’s global scan data to identify risky issues and services running on the networks where your employees are located, giving you a complete picture of your remote workforce.
With the visibility provided by these integrations, organizations can prioritize these issues for remediation and also educate users about the insecurities in their networks and how to secure them.
To learn more about ASM for Remote Workers, download the solution brief. To Learn more about Attack Surface Management, read our Cyberpedia article.