Playbook of the Week: Unleash the Power of Identity Threat Intelligence with Automation
When it comes to detecting identity-related threats, security teams need to distinguish between suspicious but benign activity and truly malicious activity. This can be challenging as identity threats and malicious insider attacks are often carried out over an extended period of time, making them harder to detect with traditional detection engines. Moreover, to effectively identify the risks associated with identity threats, organizations need a clear view of the potential risks to make informed mitigation decisions.
Because of the nature of identity attacks, a reactive approach cannot work. Security operations must be proactive against identity-related threat vectors, such as compromised accounts and malicious insiders. This means leveraging the power of AI and automation for advanced detection capabilities that enable organizations to quickly identify, investigate, and ultimately respond to identity threats.
With the new Cortex XDR Identity Threat Detection and Response (ITDR) module integration built into our existing XSOAR playbooks, you will gain the ability to enrich your SOC incident data with valuable insights into user and host identity threats. This means that you can not only detect incidents, but also understand the nuances of the risks associated with each user and host, giving you a deeper understanding of the threat landscape.
These new capabilities have been added to the Cortex XDR content pack, integrating the new Cortex XDR ITDR enhancements into the various stages of incident investigation, with alert playbooks, as well as general XDR incident playbooks.
Let's take a closer look at how these ITDR enhancements can help your security team in the case of an RDP brute-force incident. Firstly, the alert now includes identity threat data that is associated with users and hosts:
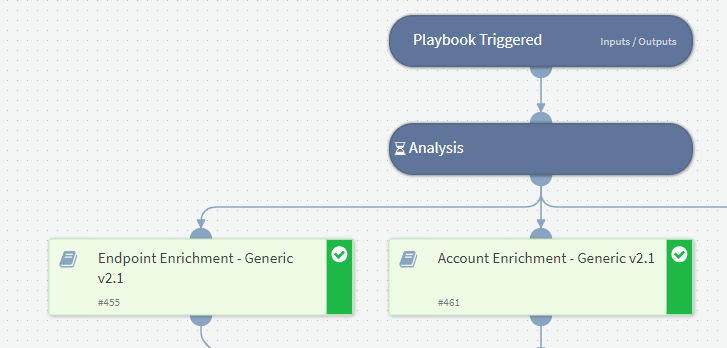
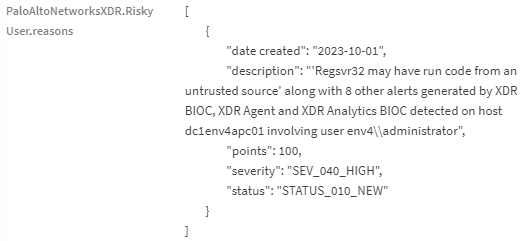
Upon examining the various detectors, analysts can see that the user "administrator" received a high risk level due to multiple reasons. One of the reasons was that "Regsvr32" may have executed code from an untrusted source, among other alerts.
The playbook responsible for setting a verdict for RDP brute-force alerts checks data from several sources, including recent activity logs of the user, the reputation of the IP from which the attack originated, and now also verifies if the user or host are risky. Since both were found to be risky in this case, the playbook will treat this alert as malicious activity.
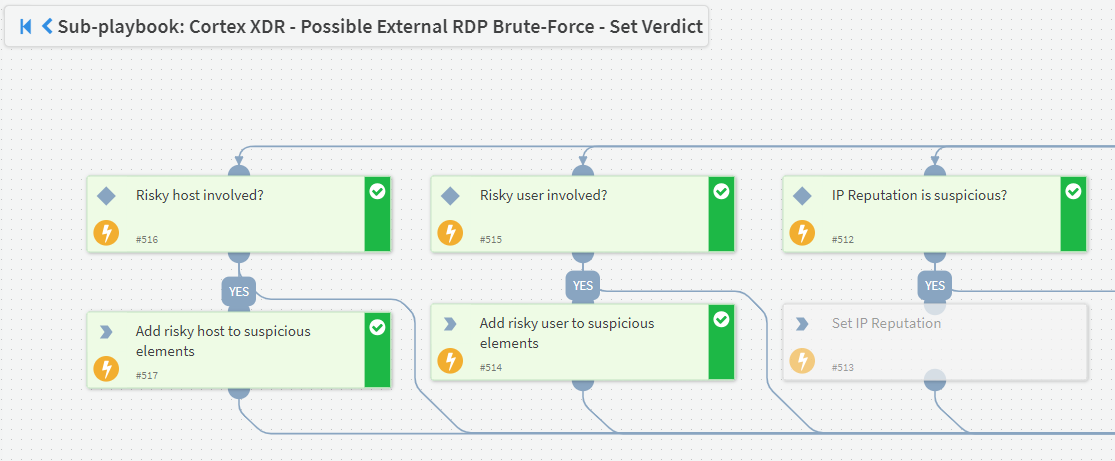
By configuring the Critical Element input of the playbook, the alert can also now be automatically escalated based on the risk level associated with the host and user identities. As a result, communications can be set automatically to the impacted user to verify the activity mentioned. Upon receiving a reply that the user did not authorize it, the analyst can then direct the playbook to proceed with the remediation.
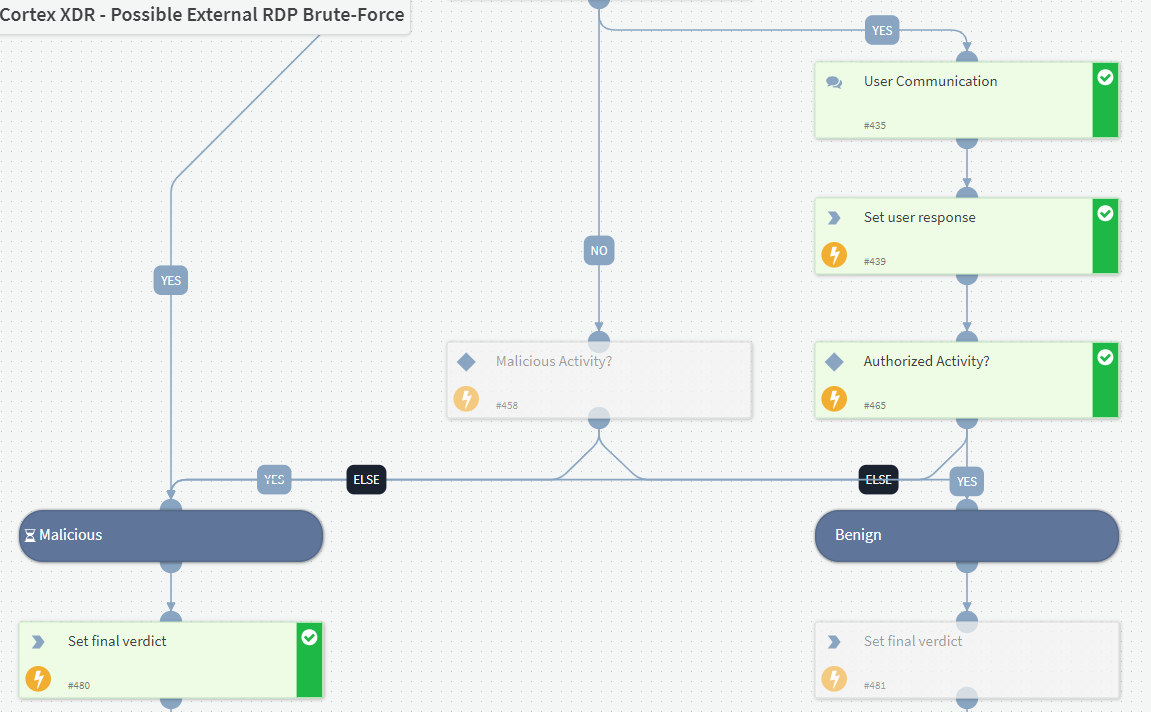
After blocking the user temporarily, the playbook provides analysts with the recommendation to isolate the endpoint due to its new identity risk.
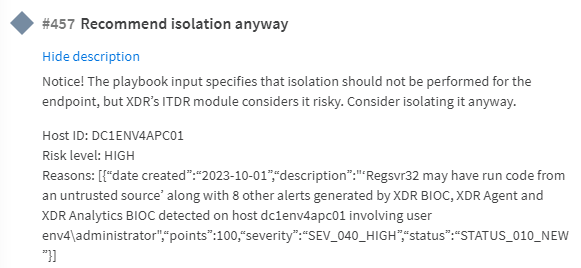
After handling the specific alert in the alert playbooks, the work plan then proceeds to the XDR Incident Handling playbook. A new severity is calculated for the overall incident based on all the information from the incident and the specific alerts, including information based on the identity threats that were identified:
As the safety of both the user and host are of utmost importance, this incident was assigned a high severity rating. To enhance transparency and facilitate better decision-making, XSOAR has a new tab in the incident layout to provide detailed information on the risky assets involved in the incident.
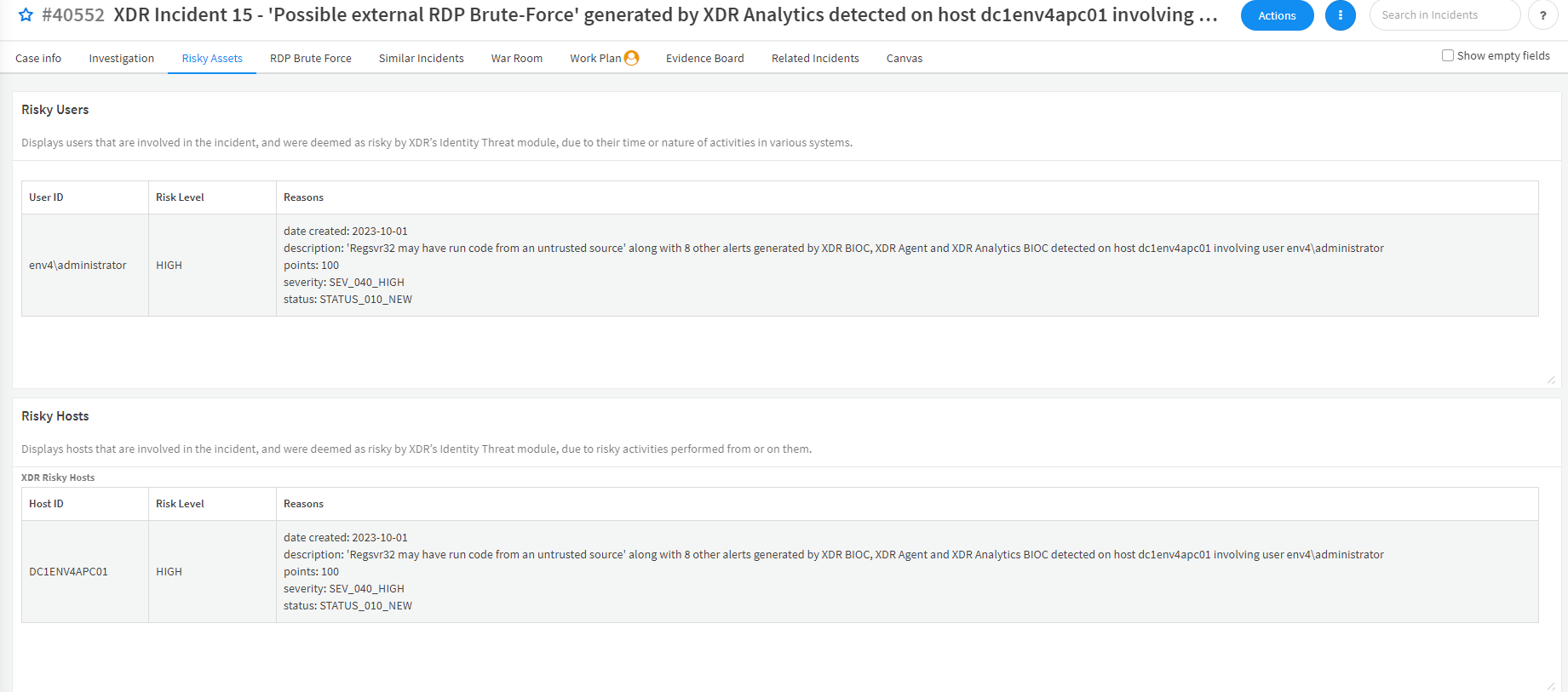
The newly added data at the alert level has led to the integration of various enhancements in alert-specific playbooks. Additionally, the improvements made at the XDR Incident Handling playbook level apply across all XDR incidents, regardless of the types of alerts they contain. This includes the enhancements to the default XDR incident layout window as shown above.
These updates are now available in XSOAR as part of the Cortex XDR content pack available via our Cortex Marketplace.
Note: These enhancements will also be made available soon in Cortex XSIAM as part of the Core - Investigation and Response content pack.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.