Last month, we announced the latest release of Prisma Cloud, a comprehensive Cloud Native Security Platform (CNSP). You can find the details in our launch blog, “Prisma Cloud Native Security Platform Embeds Security into DevOps Lifecycle.” In this blog post, we take a deeper dive into the new Compute Security capabilities that are available as part of our latest Prisma Cloud release. Compute Security is one of the four key pillars that comprise our CNSP, along with Visibility, Compliance and Governance, Network Protection and Identity Security.
Before I dive in, as a recap, there are two Prisma Cloud editions you can choose from for leveraging these new Compute Security capabilities:
- Prisma Cloud Enterprise Edition is a full Cloud Native Security Platform, where host, container, and serverless capabilities are delivered via SaaS, along with the cloud security posture management capabilities Prisma Cloud is well known for. Enterprise Edition provides a comprehensive platform for protecting both the service plane and the compute plane and can protect hosts, containers, and serverless running in any cloud, including on-premises.
- Prisma Cloud Compute Edition is the downloadable, self-hosted software that you deploy and operate on your own so that you can maintain full custody of your data. This is effectively the same experience you’re familiar with from all our previous releases. Prisma Cloud Compute Edition can protect hosts, containers, and serverless running in any cloud – including on-premises and even fully air-gapped environments.
The usual fun facts from GitHub: we’ve worked on more than 12,100 issues, pushed more than 9,200 commits, built Twistlock more than 1,400 times and shipped over 425 customer-requested features over more than four years!
While we’re highlighting new key Compute Security features in this post, we’re also shipping other features such as:
- Free form notes field to annotate every rule and result in the product.
- Integration with Cortex XSOAR.
- Direct deep linking to results across the product: email a link to the scan results of a specific image.
- IaC scanning in Compute: scan your Terraform, CloudFormation, and other Infrastructure as Code assets for compliance problems.
- Support for the latest OpenShift, CoreOS, and even dockerless environments.
Improving Host Security with AMI Scanning
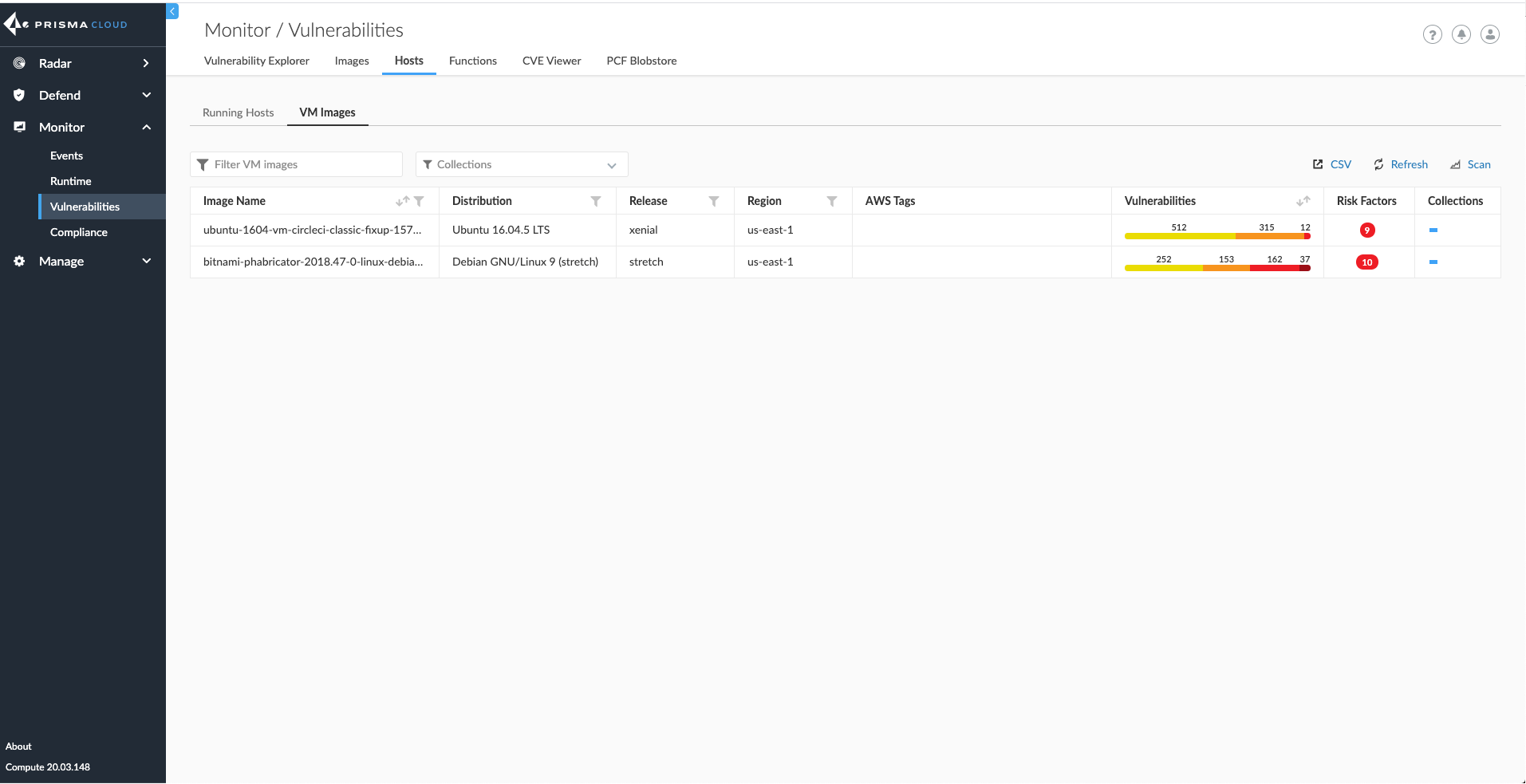
Prisma Cloud has long provided the ability to scan and continually monitor the host OS for vulnerabilities and compliance issues during CI and at runtime. These vulnerability management and compliance capabilities work in conjunction with our runtime defense, cloud native firewalling, and access control functionality – allowing users to implement file integrity monitoring, log inspection, Layer 4 and Layer 7 firewalling, and application control and whitelisting of hosts, in addition to containers and functions.
With our latest releases, we’re expanding our vulnerability management capabilities to scan Amazon Machine Images (AMIs) like we would any container repository or serverless repo. This provides DevOps and security teams with added visibility into the security posture of their AMIs, both before a deployment and in production. All policies for AMI scanning are configurable within Console.
Vulnerability Explorer v4
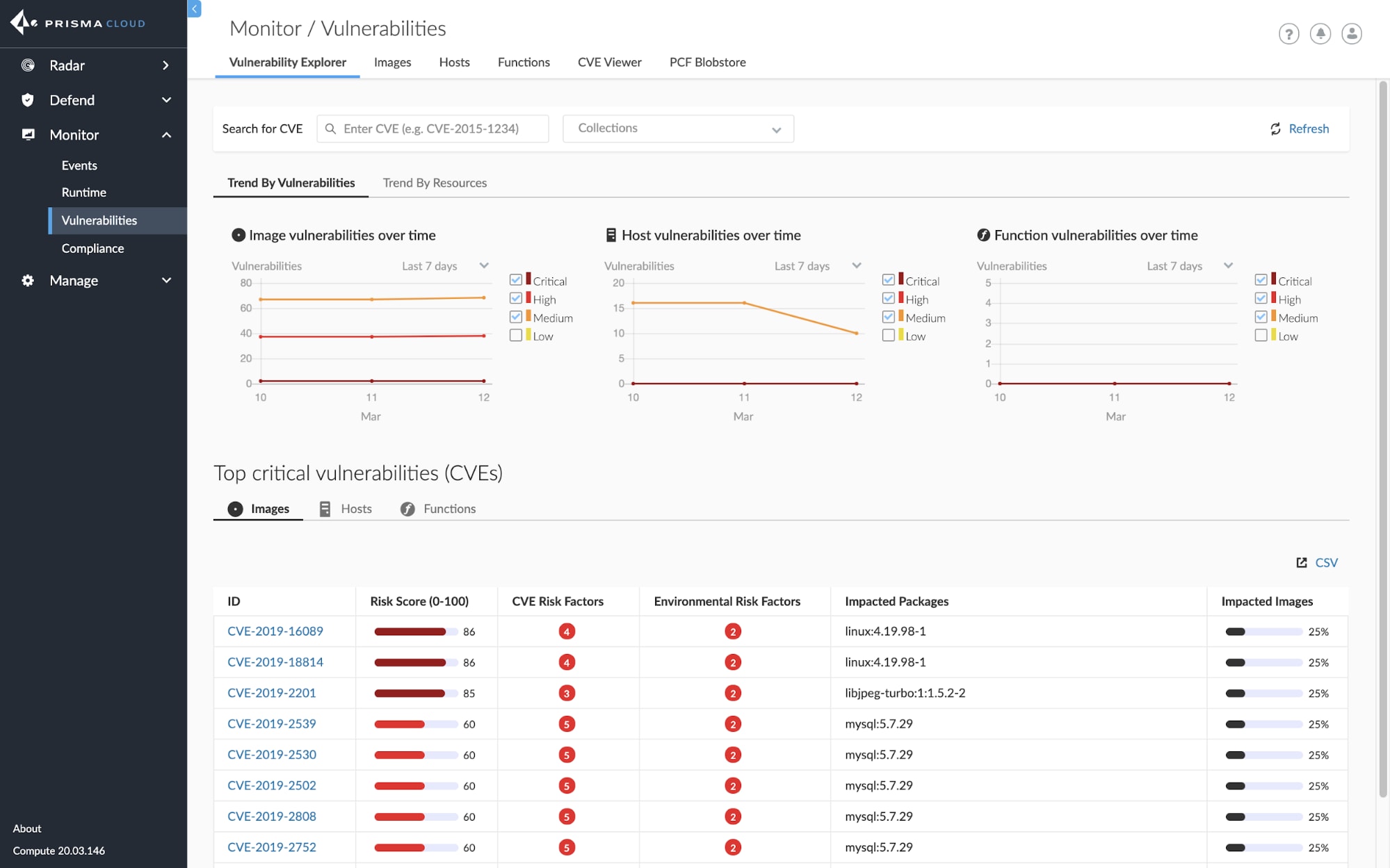
Managing risk and understanding vulnerabilities across hosts, images, and functions is a top concern for any organization today. With our latest update to Vulnerability Explorer, we’re enhancing our UI to better allow security and risk teams to quickly and easily prioritize risk across any cloud native environment.
We’ve added a top 10 list of serverless function vulnerabilities, spanning AWS, Azure, and Google Cloud, to our main dashboard so users can see top 10 lists across hosts, containers, and functions right next to one another.
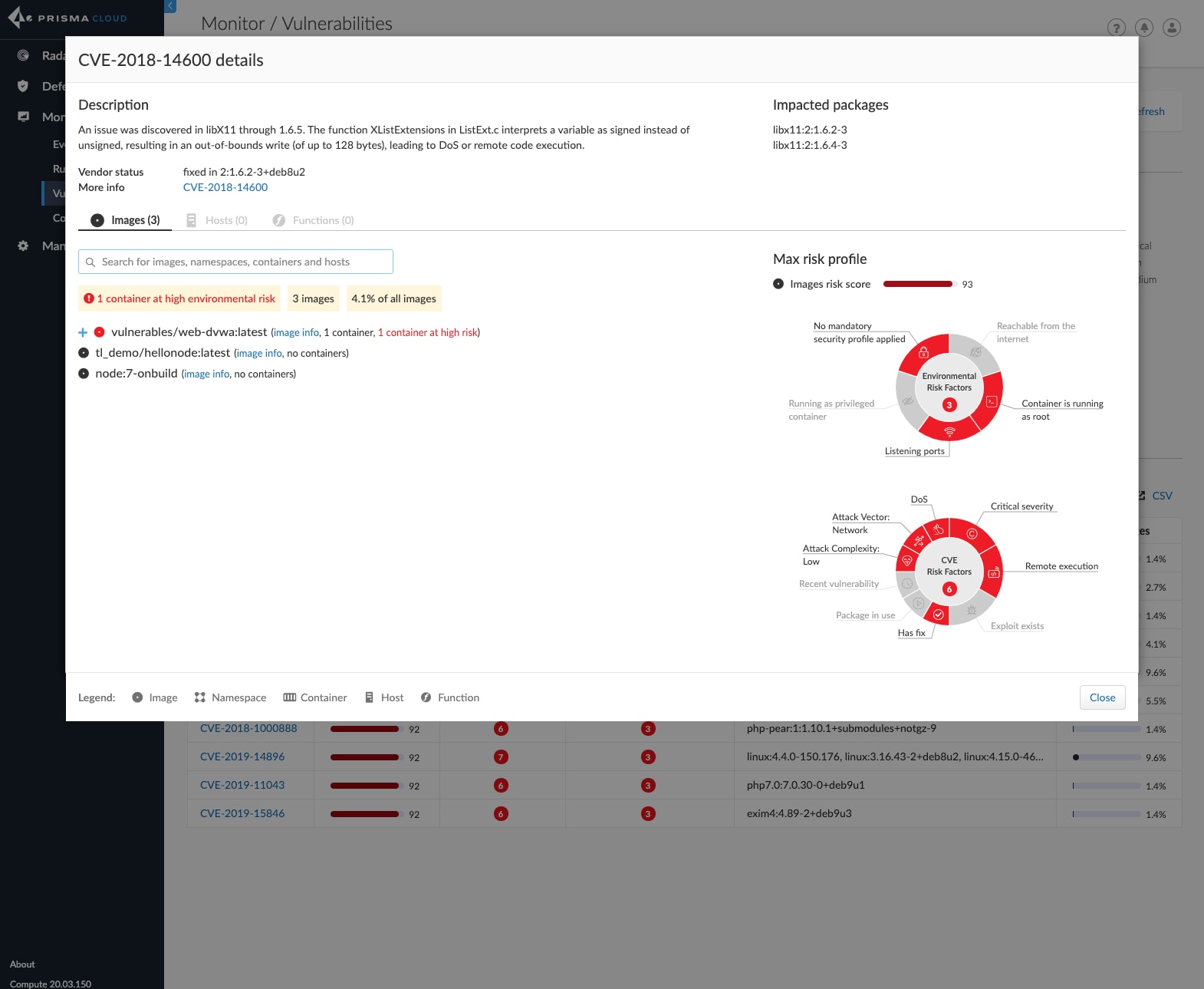
Additionally, users can now see a specific CVE spanning each compute type in a single window with an improved risk tree. The risk tree now includes new context, such as namespaces, to more easily understand which applications are impacted by a specific CVE.
Trusted Images v3
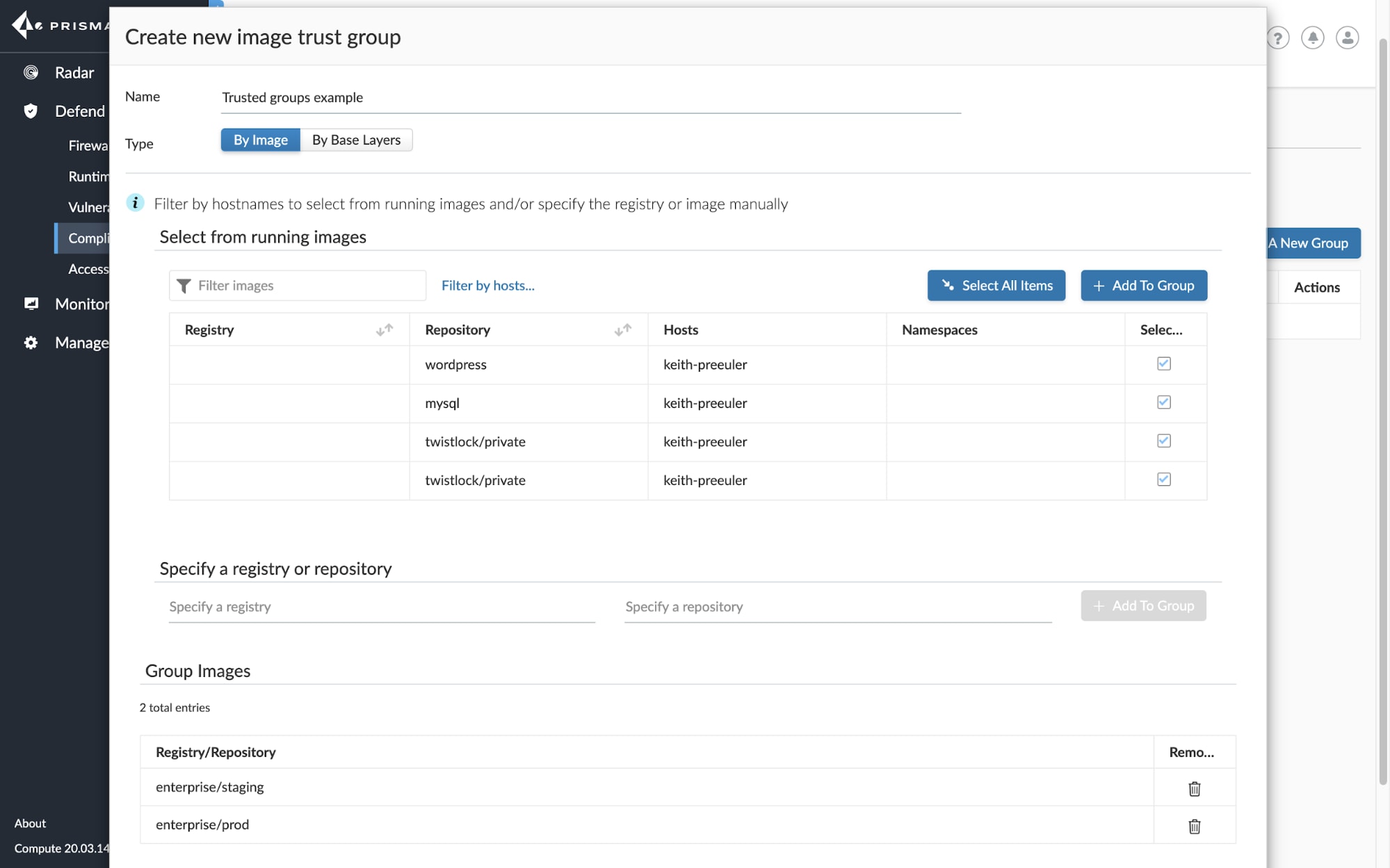
Preventing untrusted images from being deployed in any environment is a top concern for security teams. Organizations want to ensure that their images are vetted to meet vulnerability and compliance criteria and deployed from trusted sources.
With our latest update to Trusted Images, we’re providing additional support for Trusted Groups, sets of multiple images, and controls over how teams can whitelist or blacklist these images across environments. This extends these capabilities for better control over registries and repositories.
Centralizing CI/CD Policy from Console
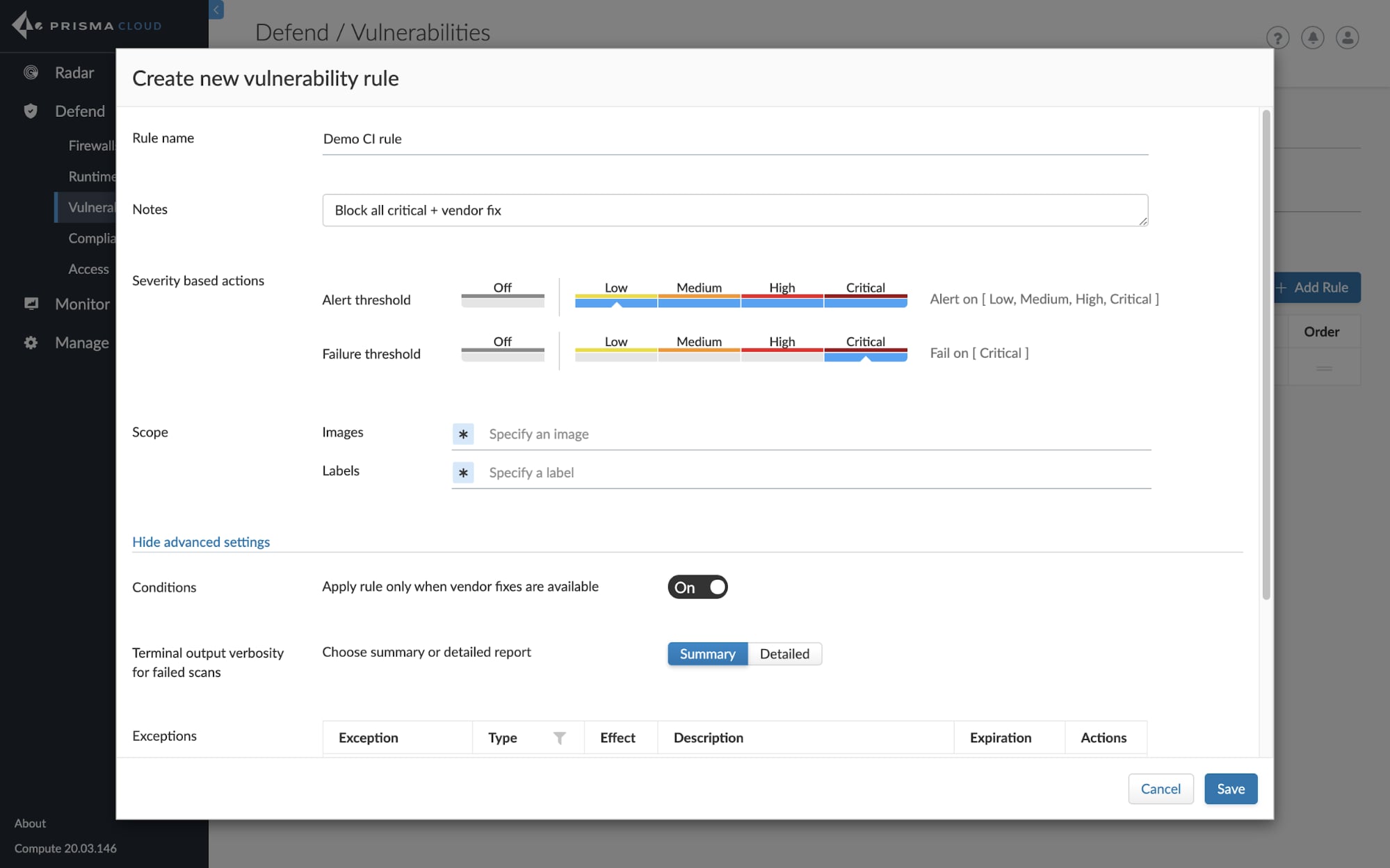
In the latest release, we’re providing the ability to set policies for vulnerability and compliance governing CI and CD workflows directly from Console. Previously, users would have to set these policies within our Jenkins plugin or as part of scripting with twistcli.
Now, users will notice a new CI tab within our Defend menu, under both Vulnerabilities and Compliance, that will allow security teams to govern their CI policies more easily. All image and function scans will be surfaced in a central location as part of Vulnerability Explorer and Compliance Explorer.
Open Policy Agent (OPA) Integration
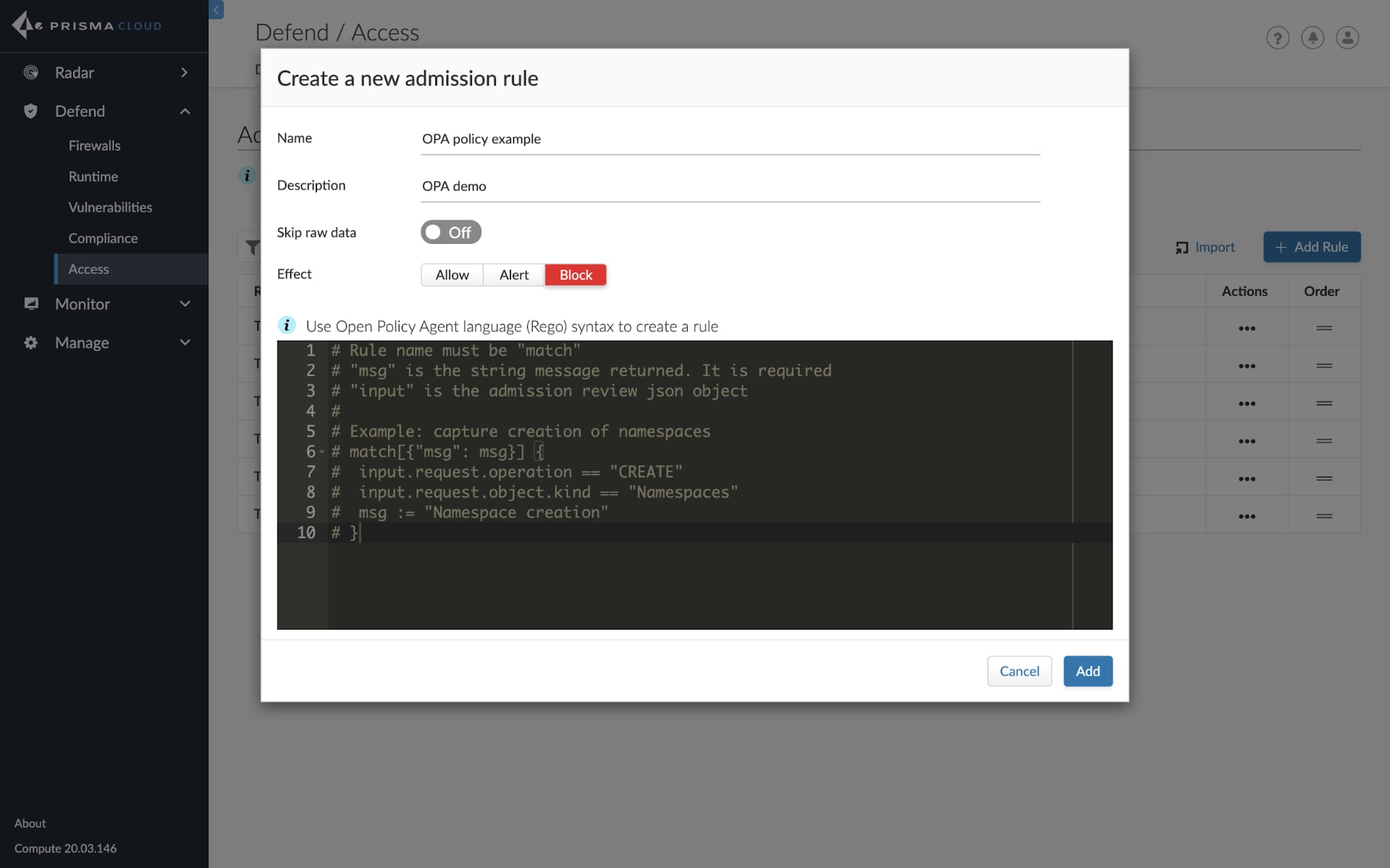
Open Policy Agent is an open source, general-purpose policy engine that unifies policy enforcement across the cloud native stack. OPA provides a high-level declarative language, called Rego, that lets users specify policy as code with simple APIs to offload policy decision-making from user software. OPA can enforce policies in microservices, Kubernetes, CI/CD pipelines, API gateways, and more.
With our latest release, we’re providing users with the ability to create policies for OPA directly from the Prisma Cloud UI and implement those policies with an admission controller. Policies can be created and managed within the Access Control policy engine and then stored in both Console and Defender.
Serverless Security: Auto-Protect for AWS Lambda Functions
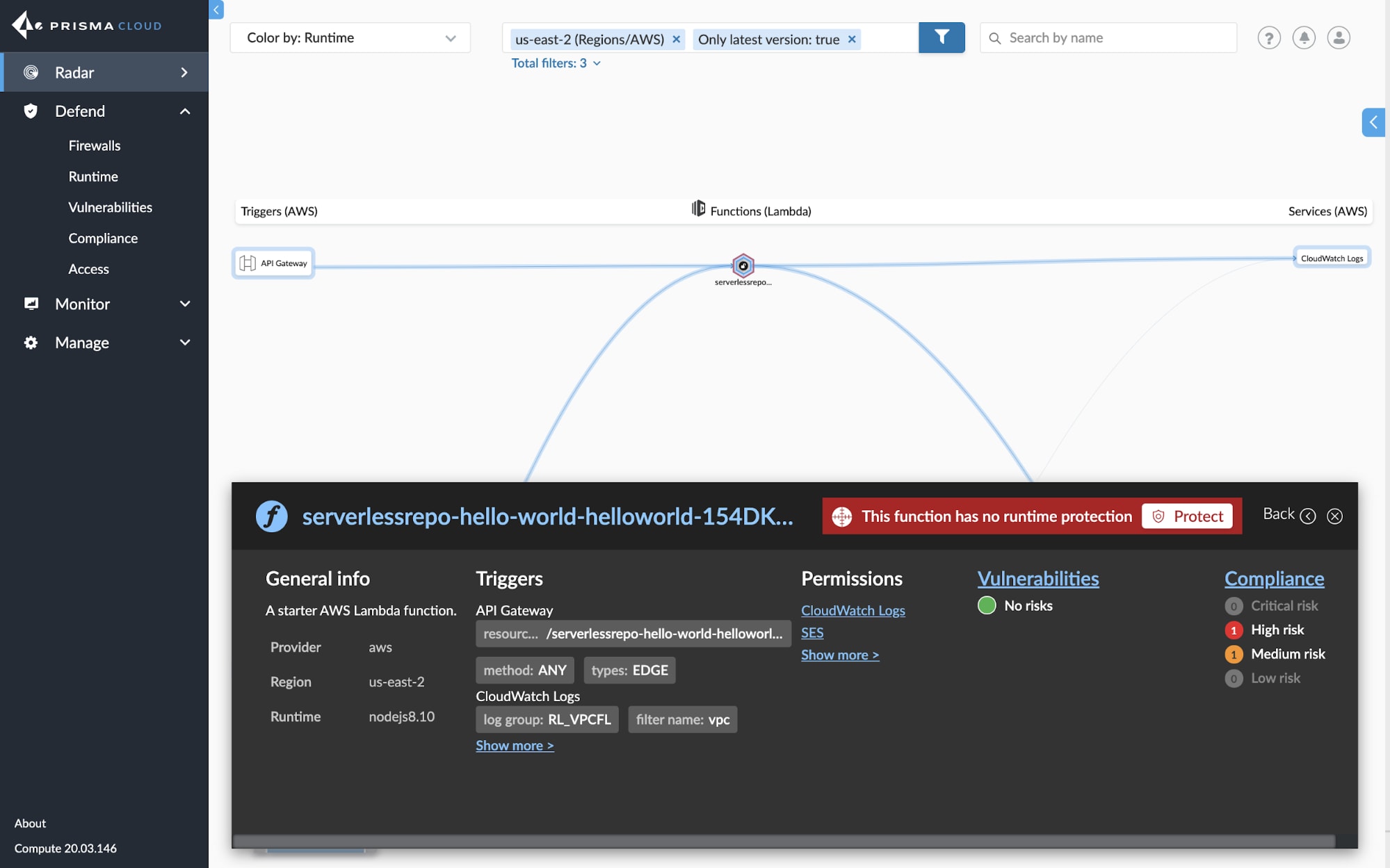
Following our expanded serverless security capabilities with our integration of PureSec in November, we’re improving the ability for security teams to better protect AWS Lambda functions being used by their organization, specifically at runtime.
While we provide runtime security today via our embedded Defender of Lambda Layer, this approach can present a challenge for security teams who need developers or DevOps teams to perform the action of implementing this agent for serverless runtime protection. With our latest release, we’re making this motion easier by providing an easy flow for serverless auto-protection directly from Console or the API.
Now, users can navigate to either Radar or the Defender deployment UI to easily identify individual functions or functions from a specific region or repo that they want to protect. Once selected, Prisma Cloud will automatically deploy the appropriate Lambda Layer to protect the function. With this release, we support:
- .NET Core 2.1
- Java 8
- Nodejs 10.x
- Python 2.7, 3.6, and 3.7
Defender Auto-Upgrade
With our unified Defender architecture, Prisma Cloud supports the ability to protect cloud native applications across standalone VMs, containers, Kubernetes, PaaS, and serverless stacks. With our latest release, we’re making the upgrades of the deployed Host and Container Defenders easier to manage from the UI or API with the ability to auto-upgrade the agents to match the version of Console. This should save users time and cycles spent redeploying Defenders to match the latest version of Console.
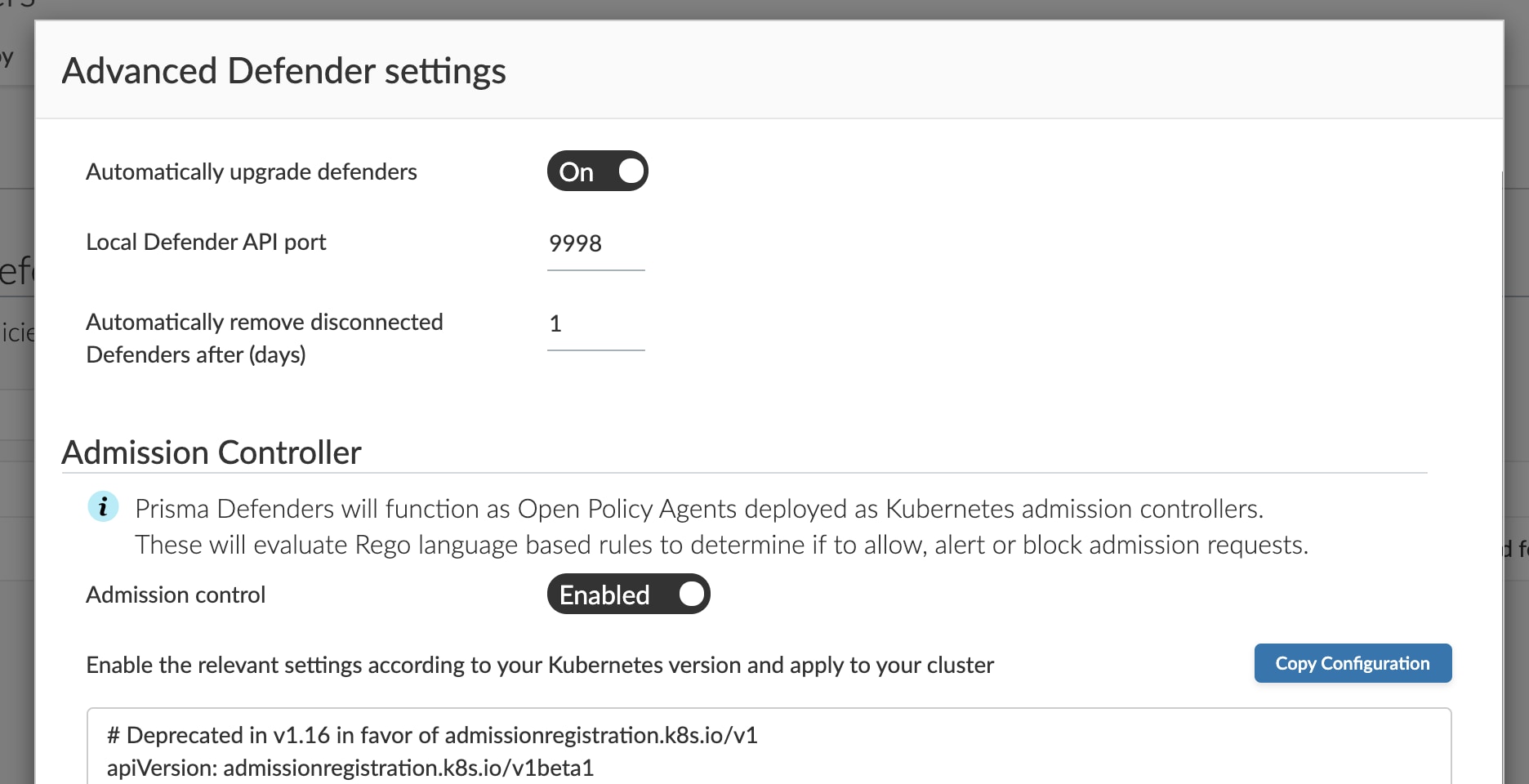
Now, users simply enable the auto-upgrade capability from the Manage > Defender UI and Prisma Cloud. This functionality supports Host Defenders, Container Defenders, and DaemonSet deployments. App-Embedded Defender and Serverless Defenders will continue to function until those applications are redeployed with the latest Defender.
Cloud Metadata Awareness
Users regularly ask us to provide cloud-specific metadata within Console. This allows users to more easily filter Prisma Cloud findings using this metadata and implement or filter policies across vulnerability management and compliance.
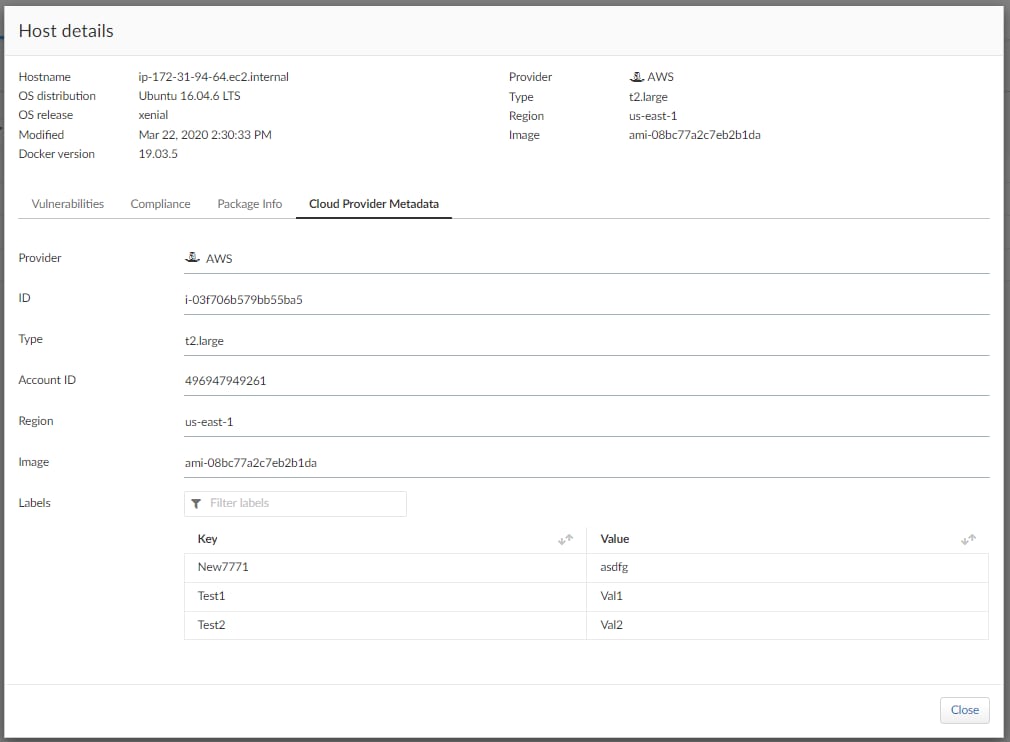
In our latest release, we’ve added the ability to:
- Ingest and surface AWS, Azure, and GCP metadata for VMs and images, along with tags for AWS Lambda functions.
- Support collections based on the metadata.
- Support filtering and implementing vulnerability and compliance policies based on the metadata.
Try It Today
See the power of all these capabilities combined – access a free trial of Prisma Cloud today!