We’re pleased to announce the latest addition to Cortex Cloud. Now you can see sensitivity labels defined in Microsoft Purview Information Protection (MPIP) for files stored anywhere in your cloud environment. This helps you identify gaps in your labeling strategy, define policies and playbooks built on existing classifications and detect potential exposure risks in real time.
How MPIP Sensitivity Labels Work
When we think of sensitive data, we might think about databases, object storage and other dedicated datastores. But a big chunk of the work is actually carried out in documents, presentations, spreadsheets and other files. These files can either be completely innocuous or contain highly sensitive information such as shareholder reports, employee personally identifiable information (PII) or confidential intellectual property.
Organizations using Microsoft’s productivity suite, such as SharePoint and Office applications, can use sensitivity labels to classify documents and define relevant data protection policies based on this classification. For example, they might decide that if a document is marked as confidential, it must be password-protected if shared externally. (We’ll refer to these labels as Microsoft Information Protection labels or MPIP labels.)
MPIP labels are embedded in file metadata and remain there regardless of where the file is stored. They form the basis of further data loss prevention (DLP) policies within the Microsoft ecosystem such as email data protection in Microsoft Outlook.
Extend and Improve Labeling with Cortex Cloud
DSPM already scans the files stored in your cloud environments – be it Azure, Amazon Web Services, Google Cloud, or SaaS applications. As part of the continuous data discovery process, Cortex Cloud DSPM now identifies and catalogs MPIP labels associated with each file. It also scans the file contents themselves, enabling you to compare the results of the Cortex classifiers – including prebuilt and custom classifications – with the label given to a specific file.
As part of your ongoing risk posture analysis, you can use the sensitivity level defined in the MPIP labels either when filtering and exploring data – to see where labeled files are stored and who has permission to access them – or when defining policies. You can also use these capabilities across Cortex Cloud, whether in remediation playbooks, CIEM workflows or other business security workflows.
Benefits of Integrating MPIP Labels
Extend Visibility
Extend visibility to wherever the file is stored. Even if a Microsoft Excel file is stored on Amazon S3 or on a virtual machine running on Amazon EC2, Cortex Cloud can identify the file contents and read the label.
Greater Value in MPIP Labels
Get more value from your existing MPIP labels. MPIP labels are often applied manually by the person generating the file, which can be an important source of insight alongside automated classifiers. Now you can gain more value from that information and use it in additional security workflows beyond those offered natively by Microsoft.
Optimize Context
Connect labeling to your broader IT and security strategy. MPIP labels are often siloed in IT and underutilized by other parts of the business. With Cortex Cloud, security teams can now use MPIP labels alongside other data profiles and risk signals across the code-to-cloud-to-SOC journey. Seeing the actual data stored in each file also helps demystify labeling schemes and better connect the label to its business objective.
Example Use Cases
1. Detect Data Exposure Risk
Scenario: A meeting summary document generated by Microsoft Word contains highly confidential information and is labeled accordingly. Due to an oversight, this document is moved to an Amazon S3 folder that is being used to store AI training data. The model trained on this data could expose the document’s contents.
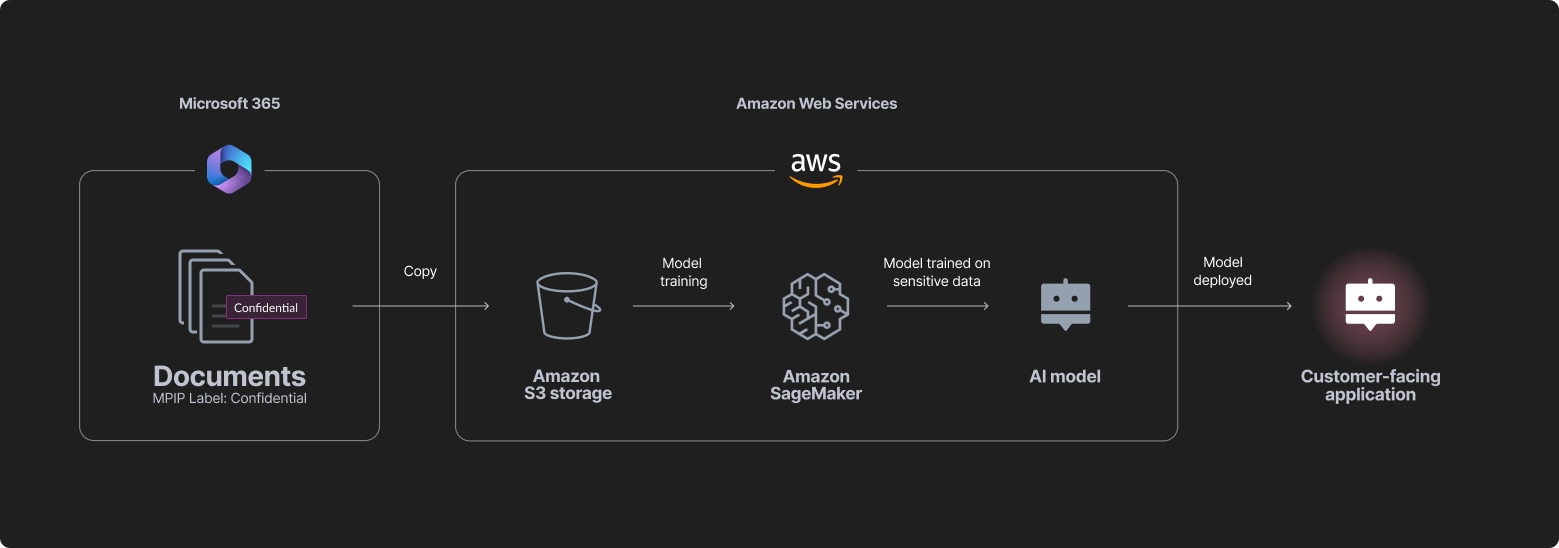
How Cortex Cloud helps: By seeing the full life cycle of the data and applications, Cortex Cloud “knows” that the folder contains AI training data. The label identifies the file as sensitive, even if classifiers looking for patterns such as customer PII miss it. Security teams can now see this risk and mitigate it by removing the file from the folder. The model itself can be retrained or disabled to remove the exposure path.
2. Find Unlabeled or Mislabeled Files
Scenario: The organizational policy dictates that files containing customer financial information must be labeled “highly confidential,” which prevents them from being shared externally. However, a finance manager mistakenly mislabels an Excel spreadsheet containing such data as “confidential,” which would then allow others to share it with contractors.
How Cortex Cloud helps: By running its own classifiers on any file found in your cloud storage environments, Cortex Cloud can identify the gap between your intended level of classification and the actual MPIP labels. You can define specific policy and playbooks to trigger when such a gap is identified.
3. Find and Fix Systemic Labeling Issues
Scenario: Marketing teams are exporting CRM data to Excel files for further analysis. These files contain customer information but are not being labeled. As a result, they could end up being shared in ways that violate compliance policies such as GDPR.
How Cortex Cloud helps: Cortex Cloud maps the specific risk to a specific data store. This helps pinpoint the problem, for example, by identifying the OneDrive location where these files are stored, which can then be traced back to the marketing department. Using this information, IT and security managers can find ways to improve education or policies and ensure that teams apply labels according to organizational expectations.
Get Started Today
Support for MPIP labels is available as part of Cortex Cloud DSPM. Contact your account manager to learn more or start with a customized demo.