Organizations typically run their applications on multiple Kubernetes clusters. Many times, different clusters are used to run the same application in different stages of the application lifecycle. In these instances, the container images are shared among different clusters, making the cluster itself an important consideration for security. Security teams need Kubernetes cluster awareness to keep track of runtime behavior and incidents, get visibility into the security posture of their deployed infrastructure and identify trusted images or manage vulnerabilities.
To better facilitate these use cases, Prisma Cloud now allows customers to leverage Kubernetes-native constructs to map rules and policies, allowing them to view runtime audits more efficiently. This means customers can segment their Radar view to specific clusters, view image scan results by cluster, define trust groups and get reliable runtime protection. Continue reading to understand how Kubernetes cluster awareness improves visibility and runtime audits.
Ensuring Accurate Runtime Protection
Prisma Cloud customers often rely on machine learning tools to detect and prevent any deviation from normal container behavior. But containers of the same application can behave differently in different stages of the application lifecycle. For example, containers run different processes in a development cluster compared to a production environment. This lack of "cluster awareness" can cause the machine learning protocols to generate false positives. Providing cluster awareness allows Prima Cloud to take this context into account. As a result, users get a more reliable, automated learning model of the runtime behavior based on the coupling of image, namespace and cluster. This significantly reduces false positives, resulting in more accurate runtime protection.
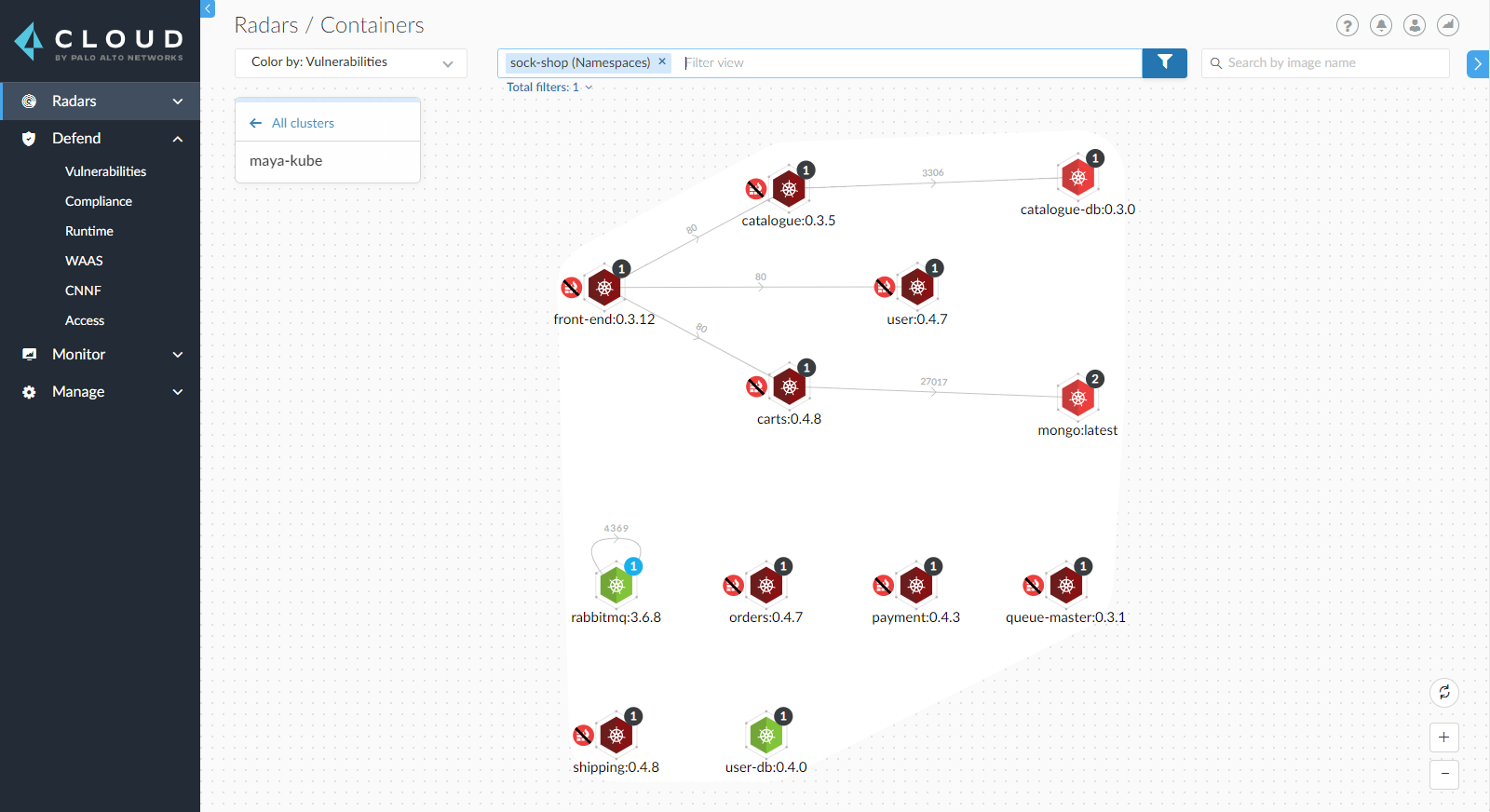
Furthermore, when security teams investigate different runtime events in Prisma Cloud, they get a more complete picture of the container including the details of the cluster.
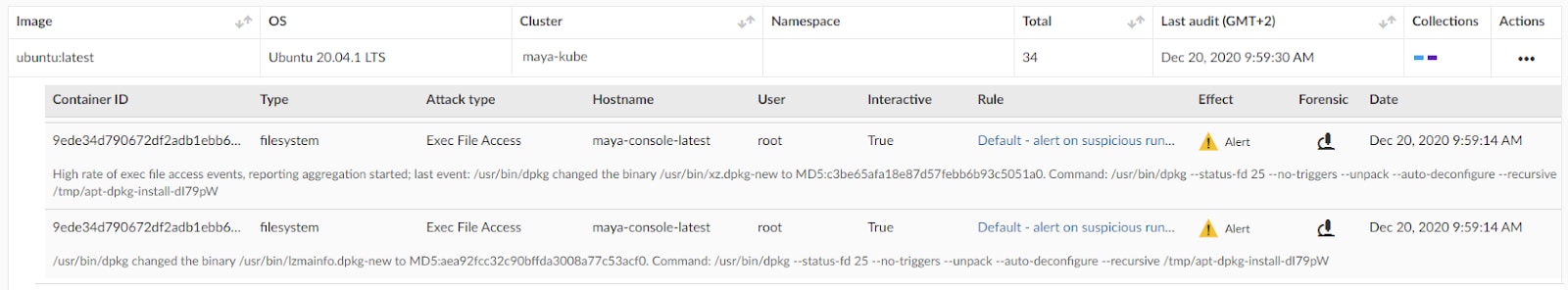
Delivering Enhanced Visibility Based on Clusters
Organizations often don't have enough visibility into the cloud infrastructure deployments supporting their applications. They lack the context on how and where the applications are running, which inhibits their ability to adequately understand their security posture. Prisma Cloud helps mitigate these blind spots by using Kubernetes native constructs to define environments and security policies. Customers can simply use the cluster pivot in Radar to build a clear map of their environment to get valuable stats as well as drill into each cluster to evaluate its attack surface, risk level and network connectivity.
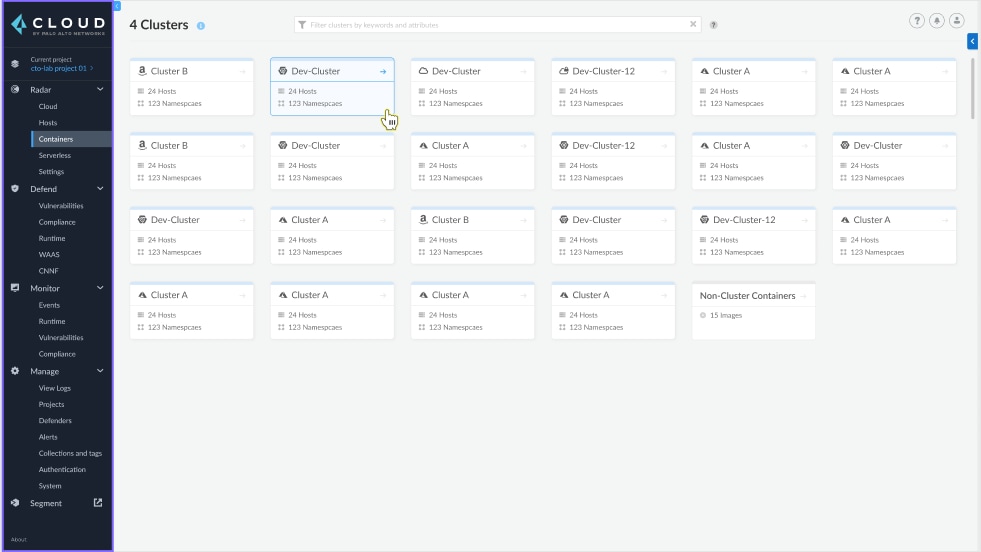
Defining Trusted Images
Defining trusted images is an important security control, and is often required by different security benchmarks. Trusted images allow DevOps or security teams to ensure images originate from a known, trustworthy source.
In order to define a good security policy for a trusted image, security teams need to take into account the cluster context. Kubernetes cluster awareness allows you to scope the rules per clusters and/or define your trust groups by checking and approving the images running on these clusters – and therefore alert or deny images that deviate from your defined trust groups
Kubernetes Cluster Awareness Is the Name of the Game
Get a deeper look at the fundamentals of container security and break down what every organization needs to know to ensure their containers—and their container environments—are secure from breaches, malware and other bad actors. Download your free copy of The 2024 Definitive Guide to Container Security. This book-length guide lays out in-depth insights and practical advice to empower developers, DevOps, cloud teams and security professionals to effectively protect their cloud-native applications.