Introduction to SmartScore
It's no secret that today, more than ever, organizations are facing an extremely difficult mission of protecting their digital assets from sophisticated cybersecurity threats. Trends such as the migration to the cloud, the shift of software workloads to mobile devices, and an increasingly remote workforce are creating a landscape with massive volumes of security data and a vast amount of alerts that SOC teams have to contend with.
Evidently, according to a recent survey conducted by Dimensional Research, 83% of the respondents stated that their security staff faces alert fatigue, and 93% of them say that they can’t address all security alerts on the same day.
To help our customers address alert fatigue, avoid wasting time chasing after false threats, and make sure no threat remains unhandled, Cortex XDR is now leveraging the power of AI and automation to deliver a top-notch automatic incident scoring engine — and make sure SOC teams using Cortex XDR spend their precious time on incidents that matter.
How Do Traditional Scoring Mechanisms Work?
Every SOC team develops its own approach to prioritizing and triaging incidents, however, the essence behind those methods is quite the same: analysts use various manual and automatic procedures to characterize a particular threat. They may score a threat in order to indicate a severity based on:
- Tactics, techniques, and procedures (TTP) classification and/or stage of the attack
- Relevance to a specific use case based on common knowledge and previous experience
- To reflect the potential impact on the target and the entire organization.
Threat intelligence is often used in parallel with those methods in order to add an additional layer of information and shed light on specific artifacts associated with the suspicious behaviors spotted to justify a deeper investigation.
But such means might have inherited flaws, as they are in most cases considered to be static and time-consuming, and even if they incorporate some sort of automation, they are missing important context to reflect the real score of the threat.
Additionally, such tools are not designed to evolve over time and adjust themselves according to the inputs of the analysts. This means incidents can reoccur with the same score over and over again, even if the analysts marked them as false positives in the past or gained new knowledge that would impact the incident score.
What is SmartScore?
Many SOC teams have developed their own systems to prioritize which incidents they will investigate first. Such systems consist of a bunch of handmade static rules that miss context, analytics capabilities, or even connection to the environment they are representing and need to be updated and maintained all the time, and as the number of rules increases, so does the maintenance effort.
Here are some examples you likely see daily:
- This alert is highly insightful but is not really precise, should I ignore it? Maybe just decrease its score?
- What should we prioritize first? How do I know where to start?
- I see this false positive again and again, didn’t I already exclude it?
Answering some of the questions above as part of your continuous prioritization workflow is not an easy task and may involve many different techniques and methods to connect the dots. With that in mind, we came up with the idea of SmartScore - A unique ML-driven scoring engine that translates security investigation methods and their associated data into a hybrid scoring system. This new disruptive system uses both ML power and contextual security rules, which are driven and built by security researchers and data scientists to generate a reliable risk score.
This risk score helps in incident triaging and threat hunting and can be also used to improve another entity scoring within an organization.
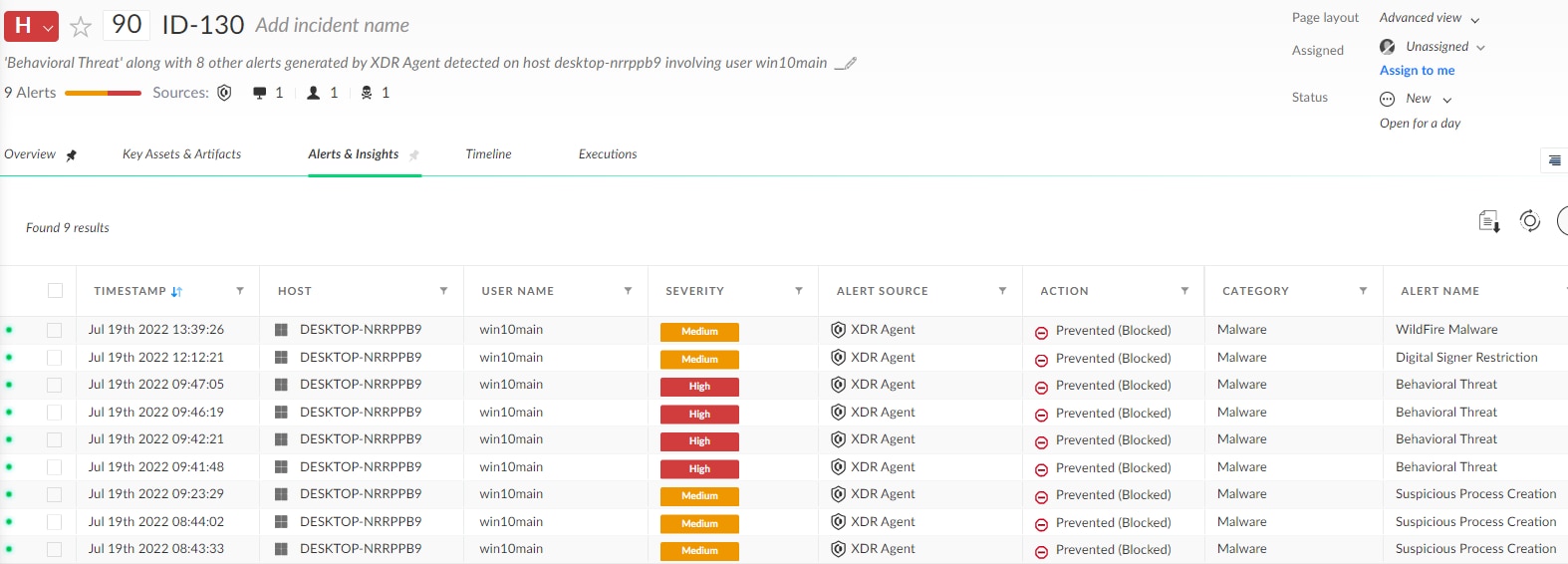
Suspicious incident found by SmartScore that received a 90 score
SmartScore, Hybrid and Manual Scoring Options
The SmartScore scoring engine improves upon the manual incident scoring capabilities introduced in Cortex XDR 2.7. It harnesses machine learning and behavioral analysis of incidents to automatically generate a risk score for each incident.
However, if you have already defined manual incident scoring rules, you can continue to use these rules alone or in conjunction with SmartScore scoring. You can use custom incident scoring rules tailored to your environment. If you use both custom and SmartScore scoring, custom scores will override scores defined by the SmartScore engine.
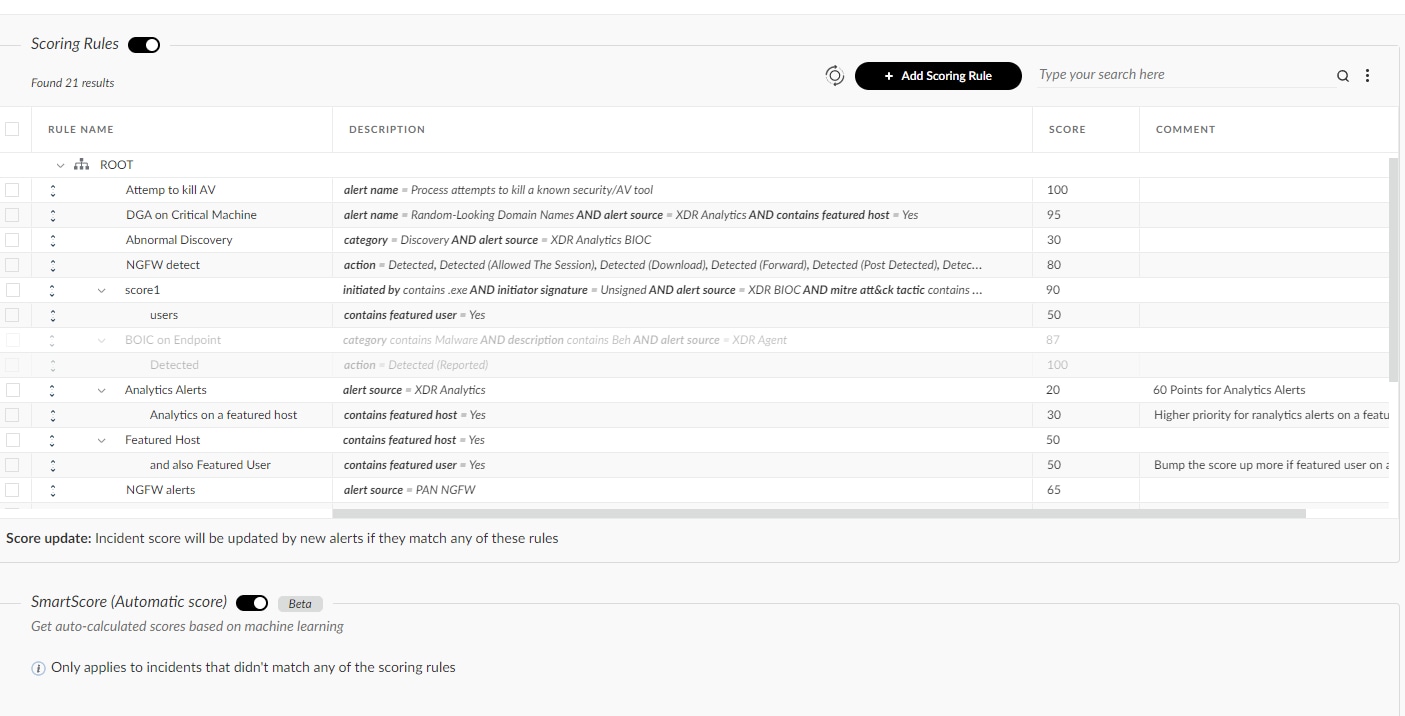
SmartScore is also adaptive to changes in your environment, not only when an incident is changed, but also when the alerts are changing their behaviors. This will allow you to invest less time in handling false positives and much more time investigating malicious cases.
Moreover, you can leverage this score with your internal security orchestration and event management systems using Cortex XDR APIs to define the set of actions that you wish to take. Our end goal is to make your life easier, make it highly effective, and allow you to spot real threats in no time.
How Does SmartScore Work?
To explain how SmartScore works, let us first define its objective in a more precise manner. In essence, we are interested in assessing the risk of potential attacks and prioritizing them accordingly. First, we have to generate these potential attack stories, containing all involved events, entities, and informational context. For Cortex XDR, attack stories are equivalent to incidents that are constructed from our own XDR alerts. These alerts may originate from a variety of sources, such as the agent, analytics engine, or NGFW alerts, with each alert describing a specific detail or artifact of the attack story. Grouping them using our incident grouping approach, we can generate a complete and meaningful attack story, compared to a narrow prism of a discrete alert. SmartScore leverages incidents as its base building block. Once an incident is generated (and every time it is updated) SmartScore predicts its risk level based on its cyber-oriented features.
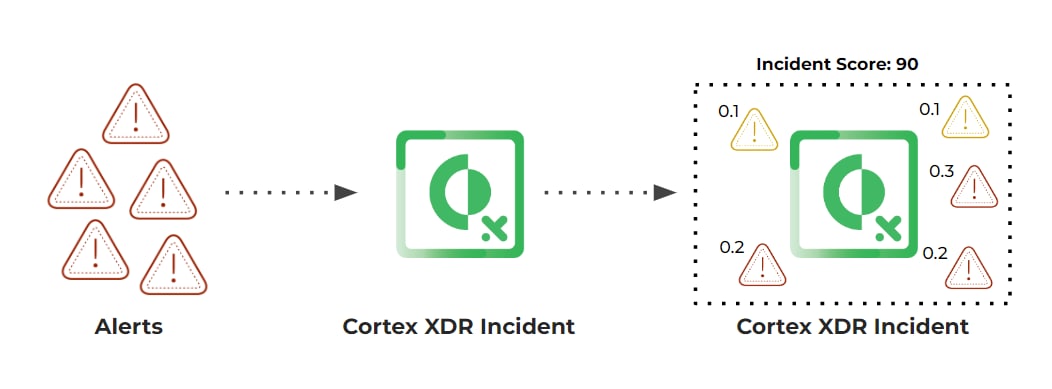
SmartScore leverages security-driven features extracted from the XDR incidents.
These include context-driven features, Incident-level features, statistical features, and model-based features.
- Context-driven features typically refer to specific alerts, their unique properties, and constantly-monitored precision, which is driven by both customer resolutions and manual research conducted by our experts.
- Incident-level features aim to quantify the overall threat statistics, for example: what the number of alerts in an incident is; what their corresponding severities are; where these alerts originated from, etc.
- Statistical features leverage the Cortex Data Lake to generate a measure of prevalence for entities of various types (files, domains, IPs, alerts, and alert combinations), both in a tenant-based and a global manner.
- Model-based features are independent ML models of their own, which focus on a specific aspect of an incident to generate a risk sub-score without being screened by any of the other artifacts. For example, we monitor the CMD process tree and assess its own risk.
Once the features are calculated, they are fed to our main ML model which consists of an ensemble of Gradient Boosting models, each designed to address a specific aspect of the data. Then, we combine the results of all models to generate a unified risk score, which is monitored by a set of contextual security-driven rules and incorporates customer-based rules and preferences.
Summary
SmartScore is a new ML-driven capability that will adapt to your environment very quickly.
Once an incident is generated, SmartScore will automatically calculate a risk score which can be observed via the UI or the API. SmartScore can help your SOC not just fight against alert fatigue, but also remediate real threats faster, and reduce the overall mean-time-to-respond (MTTR). With SmartScore, organizations can speed up triage, prioritization, and incident response and make sure no real threat is being left unnoticed. Its unique ecosystem, as well as its ability to learn dynamically from our users’ input, help us to keep improving the models behind the scenes and adjust the scores in a timely manner.
How Do I Opt-in?
Wish to join us on this journey? All you need to do is turn SmartScore on, and start working on the incidents that really matter! You can enable SmartScore from the Incident Response > Incident Configuration > Incident Scoring page in the Cortex XDR console.
To see all our latest Cortex XDR features in action, including SmartScore, attend our webinar, “Forward Together: Cortex XDR and Unit 42 MDR” on August 16.
