Written by Eli Birkan, Gal De Leon, and Niv DavidPur
Understand How Cortex XDR and Cortex XSOAR Protect Organizations Against Follina Zero-Day Exploits
In the last few days, a zero-day abusing Microsoft Support Diagnostic Tool (MSDT) protocol handler was caught being exploited in the wild. The zero-day vulnerability, dubbed Follina, was discovered by accident after a researcher found a malicious Microsoft Word document submitted to VirusTotal from an IP address in Belarus.
Further analysis revealed that the malicious document abuses a zero day vulnerability in Word to execute a PowerShell payload. Soon after the malicious document was shared, multiple security researchers successfully reproduced the exploit on Microsoft Office 2003 through the current version (https://github.com/chvancooten/follina.py). Additional analysis showed that similar files dating back to April 2022 were observed in Russia-Ukraine cyber activity.
How Does the Vulnerability Work?
CVE-2022-30190 is a zero-day vulnerability in the MSDT component. At the time of writing, a patch does not exist for this vulnerability; a proof-of-concept exploit is publicly available, and Microsoft reported it is being actively exploited in the wild.
Using this vulnerability, attackers can run malicious code on the victim’s endpoint through malformed MS Office documents. The vulnerability is similar to CVE-2021-40444 but abuses the MSDT protocol handler (ms-msdt) to achieve remote code execution (RCE).
Our researchers analyzed multiple samples of this exploit and observed the following behaviors:
- When the malicious document is opened, Microsoft Office downloads an HTML file from a remote server and executes it. Alternative vectors of attack could also work with Internet Explorer, Microsoft Edge, and even PowerShell’s “wget” command.
- The HTML file contains JavaScript code that uses MSDT protocol handler.
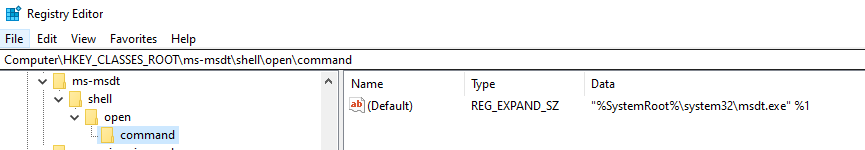
(Figure 1 - ms-msdt protocol handler definition in registry)
3. Using the ms-msdt protocol handler, the attacker is able to control the arguments passed to msdt.exe, which is spawned by winword.exe.
4. Msdt.exe runs the troubleshooting pack for Program Compatibility Wizard (PCW), which executes the script ‘C:\Windows\diagnostics\system\PCW\TS_ProgramCompatibilityWizard.ps1’ in the context of sdiagnhost.exe. That script gets one of its arguments, IT_BrowseForFile, directly from msdt.exe’s command line which is controlled by the attacker.
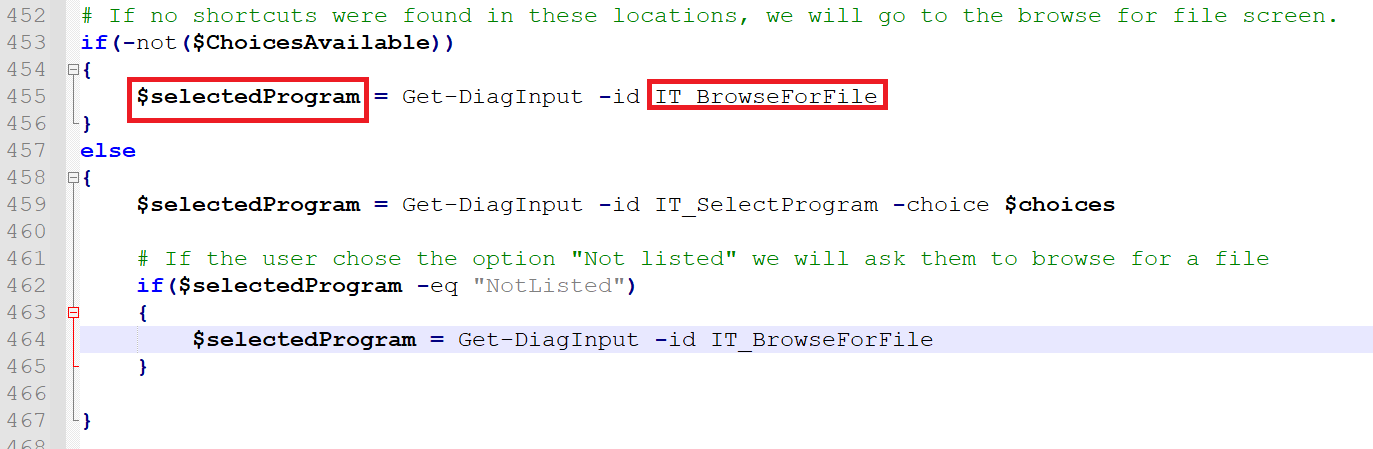
(Figure 2 - Snippet from TS_ProgramCompatibilityWizard.ps1 that fetches IT_BrowseForFile parameter)
5. After some validation on the contents of “IT_BrowseForFile” argument, TS_ProgramCompatibilityWizard.ps1 calls Update-DiagRootCause cmdlet to set the diagnosis root cause. That cmdlet gets the forged argument in the “TARGETPATH” parameter.
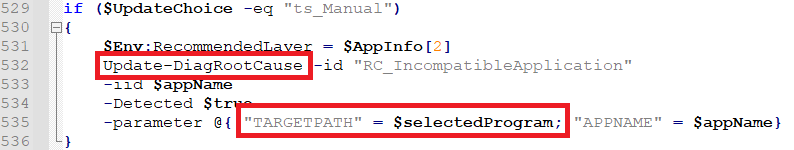
(Figure 3 - Passing parameters to Update-DiagRootCause cmdlet)
6. Update-DiagRootCause then calls RecordRootcause, which triggers another script execution from msdt.exe to sdiagnhost.exe in Rootcause::Resolve.
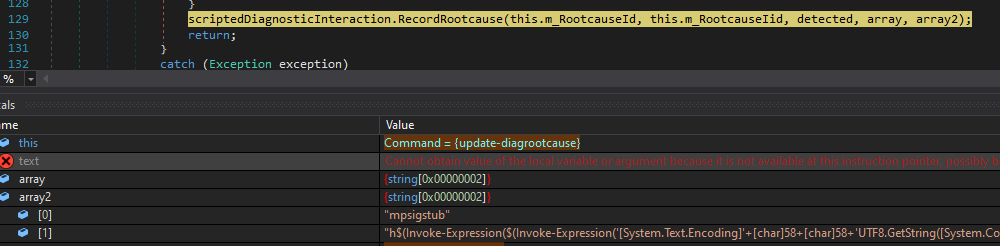
(Figure 4 - Update-DiagRootCause in sdiagnhost.exe calls RecordRootcause)
7. The sdiagnhost.exe application executes ‘C:\Windows\diagnostics\system\PCW\RS_ProgramCompatibilityWizard.ps1’ script. Before the script is executed, PowerShell’s engine evaluates the value of TARGETPATH parameter as a valid PowerShell statement, which essentially allows command injection and execution of arbitrary PowerShell code.
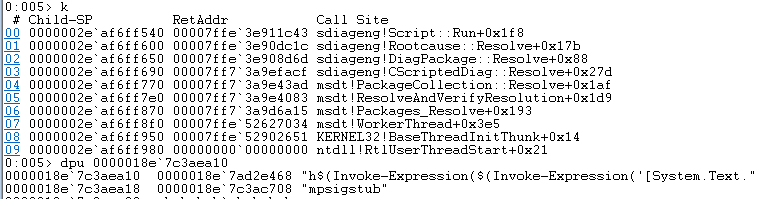
(Figure 5 - malicious args passed by Rootcause::Resolve in msdt.exe)
8. Any malicious activity on the machine will be spawned by sdiaghost.exe.
Cortex XDR Agent 7.5 (and above) prevents this threat with the Behavioral Threat Protection module (starting from content version 540-92526) with the following alert:
Alert Name: CVE Exploitation - 3609678030
Description: Follina variant - Behavioral threat detected (rule: msdt_exploit)
Hunting for This Attack in Your Environment
You can hunt for this attack using XQL Search in Cortex XDR.
// office processes spawning msdt.exe
config case_sensitive = false timeframe = 30d
| dataset = xdr_data
| filter event_type = ENUM.PROCESS and action_process_image_command_line contains "msdt.exe" and actor_process_image_name in ("winword.exe", "powerpnt.exe", "excel.exe", "msaccess.exe","visio.exe","onenote.exe","powershell.exe")
| fields agent_hostname , action_process_image_command_line , action_process_image_path , actor_process_command_line , actor_process_image_path , causality_actor_process_image_path
// msdt.exe execution with suspicious argument
config case_sensitive = false timeframe = 30d
| dataset = xdr_data
| filter event_type = ENUM.PROCESS and action_process_image_command_line contains "msdt.exe" and
action_process_image_command_line contains "it_browseforfile"
| fields agent_hostname , action_process_image_command_line , action_process_image_path , actor_process_command_line , actor_process_image_path , causality_actor_process_image_path
How Cortex XSOAR Can Help
Our mission has been to help our customers automate security operations as much as possible – a key part of staying ahead of today’s automated attackers. To help with this, we provide playbooks for specific types of response, maintain an ecosystem where others can contribute playbooks as well, and we advise our customers to add our playbooks to their SecOps process to automate what they can.
For this attack and many others, organizations can leverage the power of automation with Cortex XSOAR to help speed up the discovery and remediation of compromised hosts within the network. XSOAR automated playbooks aid in unifying threat feed ingestion, indicator enrichment, and incident management workflows, helping your team respond to attacks at machine speed.
The "CVE-2022-30190 - MSDT RCE" playbook includes the following tasks:
- Collect detection rules.
- Exploitation patterns hunting using Cortex XDR - XQL Engine and 3rd party SIEM products.
- Cortex XDR BIOCs coverage.
- Microsoft workarounds and detection capabilities.
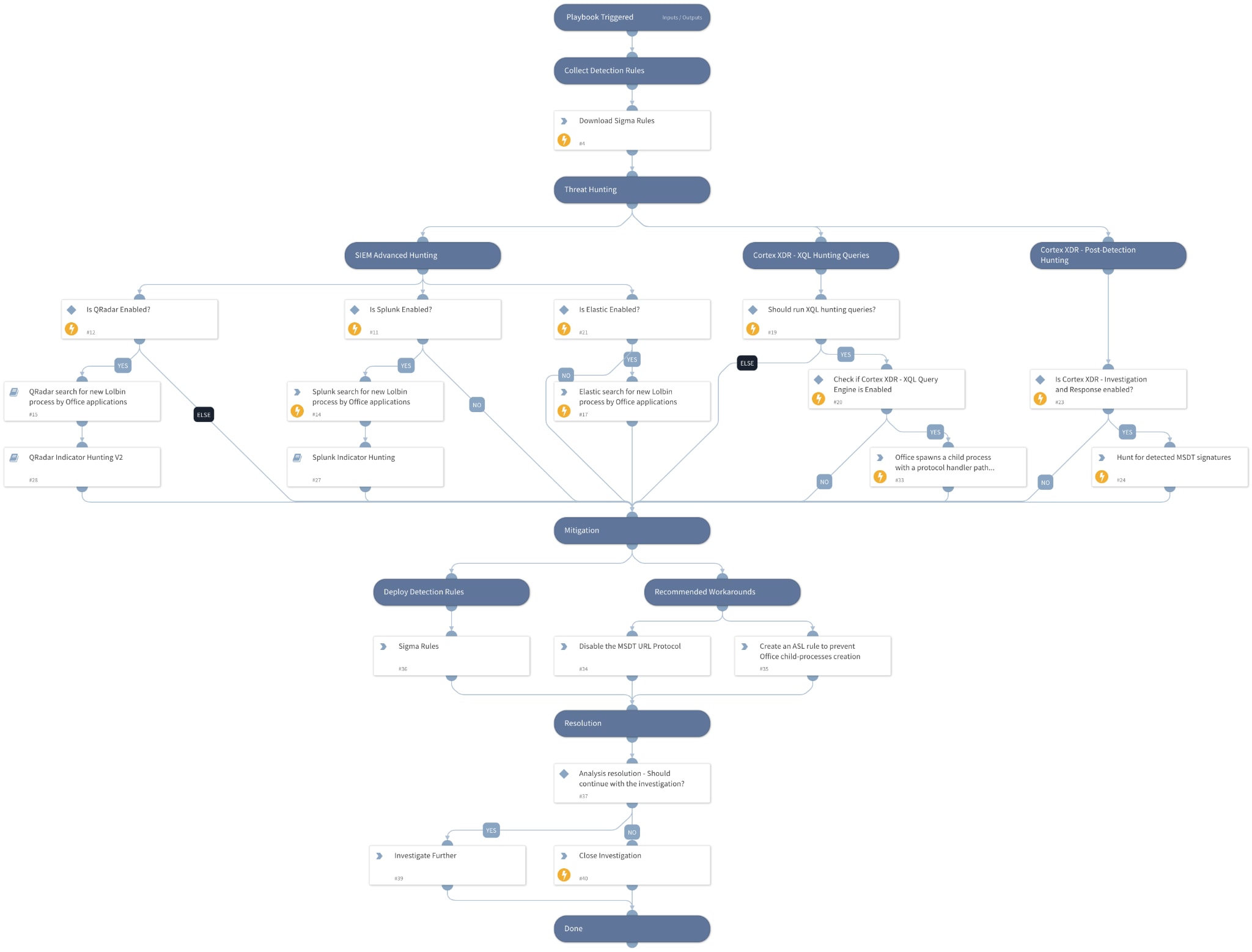
(Figure 6 - “CVE-2022-30190 - MSDT RCE” playbook)
Conclusion
The Follina MSDT code execution vulnerability is a critical vulnerability that enables remote code execution with the same privileges as the calling application.
We recommend following Microsoft’s guidance to protect your organization until a patch is issued. Once a patch is released by Microsoft, we recommend installing the patch on all affected systems.
You can also rely on Cortex XDR and Cortex XSOAR to hunt for and block attacks associated with the MSDT code execution vulnerability. Cortex XDR Agent 7.5 and higher (with content version 540-92526) prevents attempts to exploit this vulnerability with the Behavioral Threat Protection. In addition, Cortex XDR lets you hunt for signs of attack in your environment. Cortex XSOAR automated playbooks help your team respond to attacks quickly by unifying threat feed ingestion, indicator enrichment, and incident management workflows.
Want to learn more about Cortex XDR and Cortex XSOAR? Visit the Cortex XDR and Cortex XSOAR web pages.
References:
- Threat Brief: CVE-2022-30190 – MSDT Code Execution Vulnerability
- Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability – Microsoft Security Response Center
- Security Update Guide - Microsoft
- Using Cortex XSOAR to Deal With MSHTML Zero-Day Vulnerability (CVE-2021-40444) | Palo Alto Networks