Harnessing the Power of UEBA for Cloud Security
This post is also available in: 日本語 (Japanese)
Implementing cloud security is a critical piece of every organization’s journey to the cloud. As organizations expand their cloud footprints across infrastructure as a service (IaaS) and platform as a service (PaaS) capabilities that span multiple accounts and regions, and grant privileged access to multiple users across this vast landscape, it becomes apparent that monitoring user activity is an essential requirement during their cloud journey.
When it comes to monitoring user behavior, ultimately we are looking for signs of two things:
- Potentially compromised credentials.
- Malicious insider threats.
In the hands of a skilled attacker, compromised credentials can be used to wreak havoc in your environment. Leveraging a user and entity behavior analytics (UEBA) engine, which is a key feature of any Cloud Native Security Platform (CNSP), you can identify sensitive activities such as risky privileged (or root) user behavior, security group changes and identity and access management (IAM) configuration updates; these may be indicators of compromised credentials or insider threats. With early detection, you can stop these attacks before they get to the point of compromise in your cloud environment.
Monitoring User Behavior without UEBA
Where do you start if you don’t have UEBA deployed? Typically, by using the investigative tools and capabilities the cloud providers offer. Each cloud service provider (CSP) provides governance, compliance, operational auditing and risk auditing capabilities to evaluate their own cloud environments. This is done through event history, using audit logs, such as CloudTrail for AWS, Azure Activity Log or Google's Stackdriver Logs. With the audit logs, you are able to view a historical list of activities in your cloud environment, as well as who performed these activities.
Manually reviewing these logs is time and resource-intensive, especially in a multi-cloud environment, which is why many customers typically send them over to a tool such as a security information and event management (SIEM). Here they can begin to analyze and query the data to find out more information, establish patterns and investigate events. Unfortunately, this process simply does not work well with the public cloud. Too much data is being generated and there is a complete lack of cloud context in the process. It’s unrealistic to try to make effective security decisions based on this data. Therefore, your best option for doing this effectively is to employ machine learning (ML) capabilities, like that of Prisma Cloud, or another CNSP.
UEBA with Prisma Cloud
With Prisma Cloud, you can leverage ML to take the human element out of finding indicators of compromise (IoCs) in your cloud environment. The UEBA engine uses an autonomous system to monitor the logs coming in from various sources in order to establish a baseline of “normal” activity, and based on this model it has built, it begins to call out what is unusual behavior. Prisma Cloud uses this data to alert the security or security operations center (SOC or SecOps) with the behaviorally unusual findings.
Due to the fidelity of the alerts, this tremendously helps reduce the burden on the already overwhelmed cloud SOC teams since it provides rich cloud context such as who made what change, in what time period, using which device, on which resource, from what location and what was the result of that change. Additionally, when reviewing alerts of this nature, you want to be able to investigate the surrounding events that lead to the alerts. Prisma Cloud’s dynamic investigation capabilities allow you to quickly uncover details surrounding anomalous alerts and even the patterns that were established before the alert was generated.
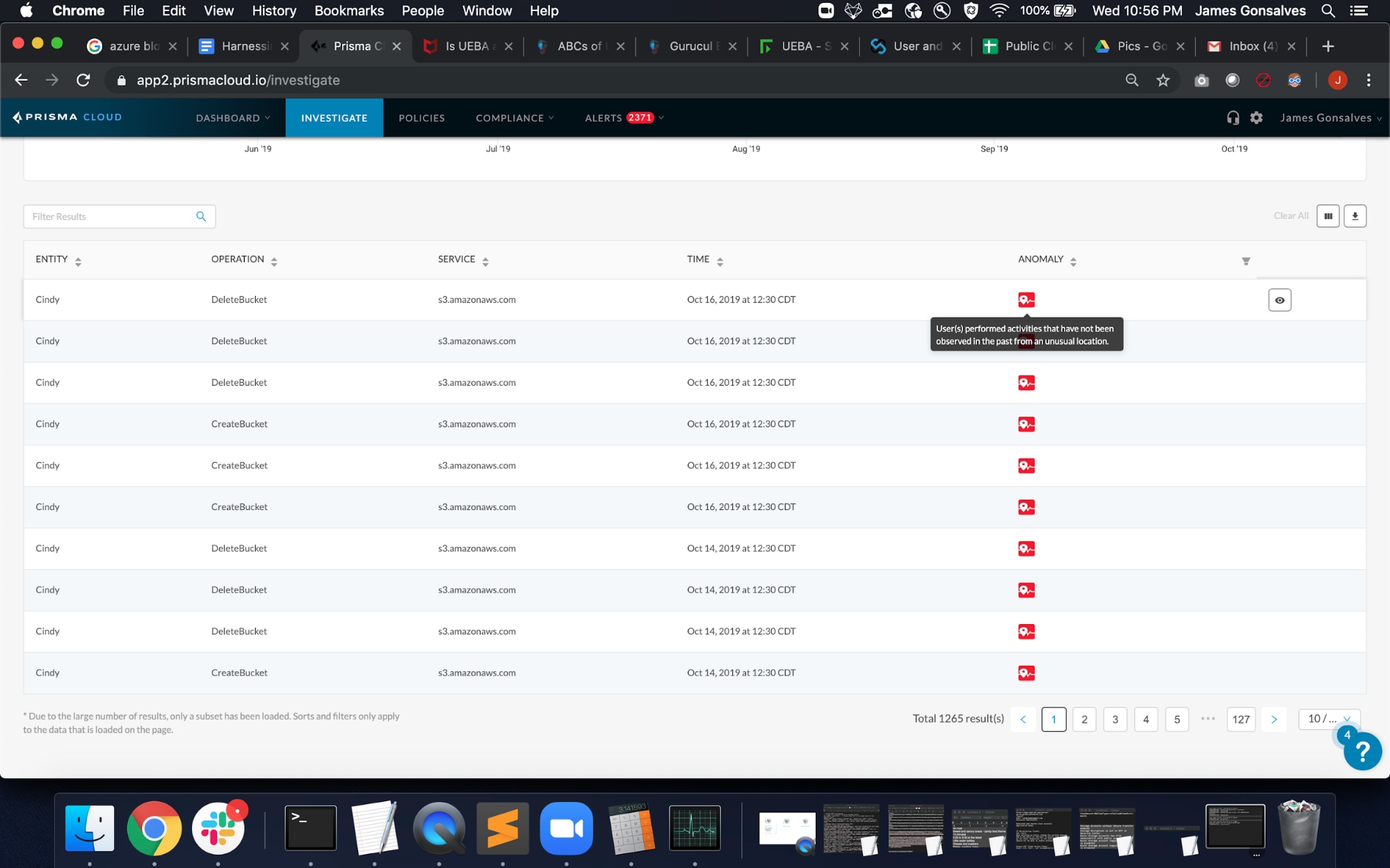
The machine-intelligence-built model takes into consideration a deep variety of details, such as the device used, the location of the user when accessing services, the cloud service being accessed, the location of the user, the source IP address and whether the activity was performed during or outside of the user’s typical work hours.
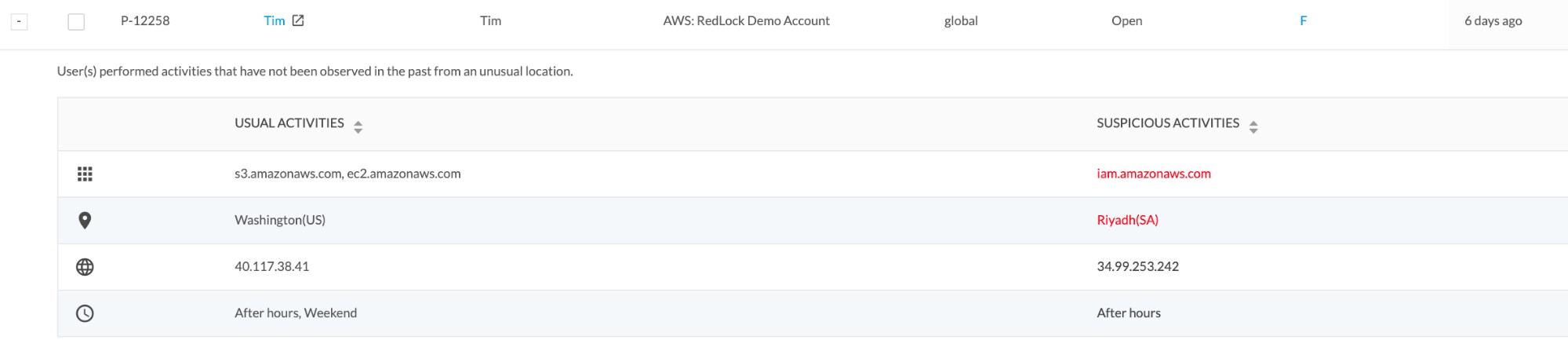
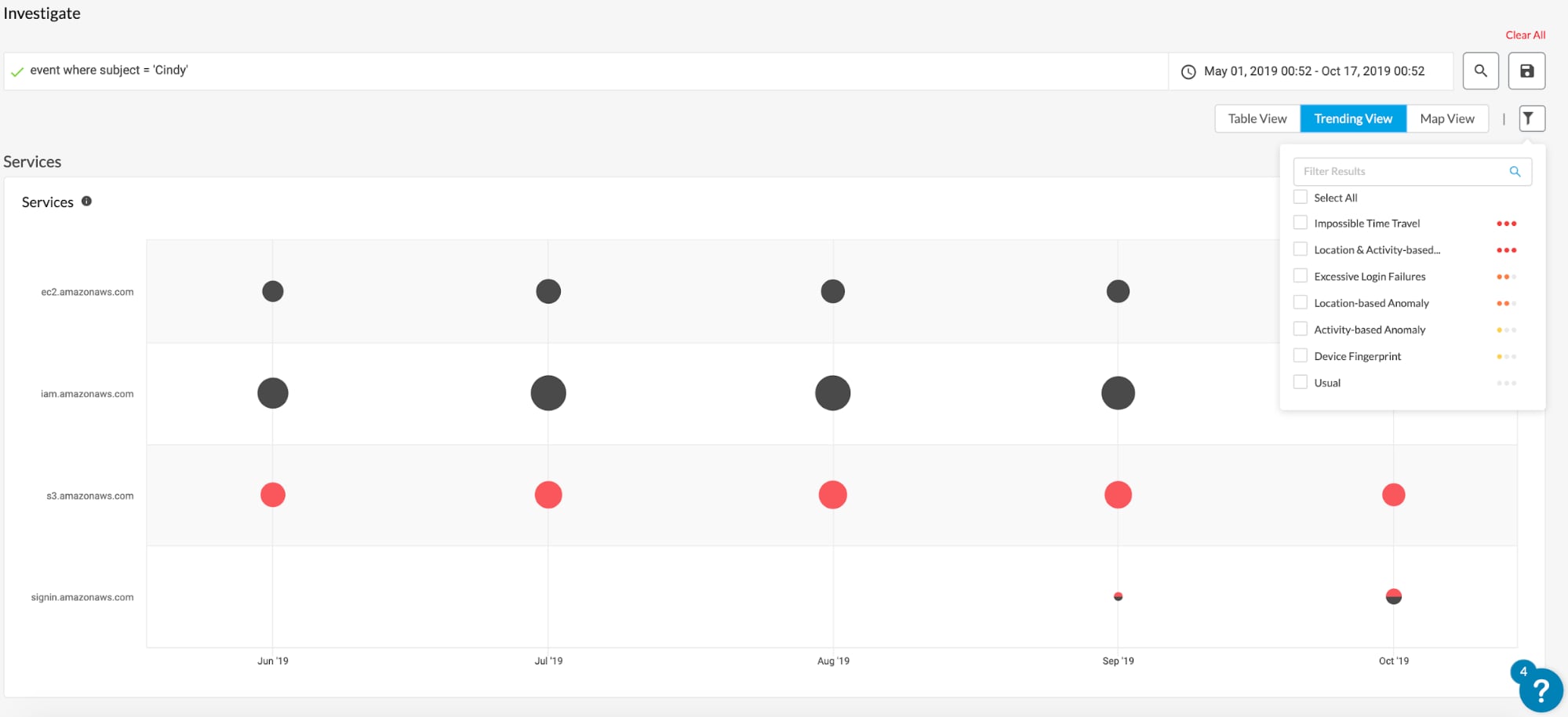
At a high level, the alerts are generated based on an unusual location, an unusual activity that the user is performing, or a combination of an unusual activity being performed from an unusual location. Prisma Cloud categorizes these anomalous user and entity behaviors into the following three categories: unusual user activity, excessive login failures and account hijacking attempts or brute force attacks.
When investigating these alerts, the cloud SOC team can quickly uncover the extent of the unusual activity by viewing it across their cloud environment.
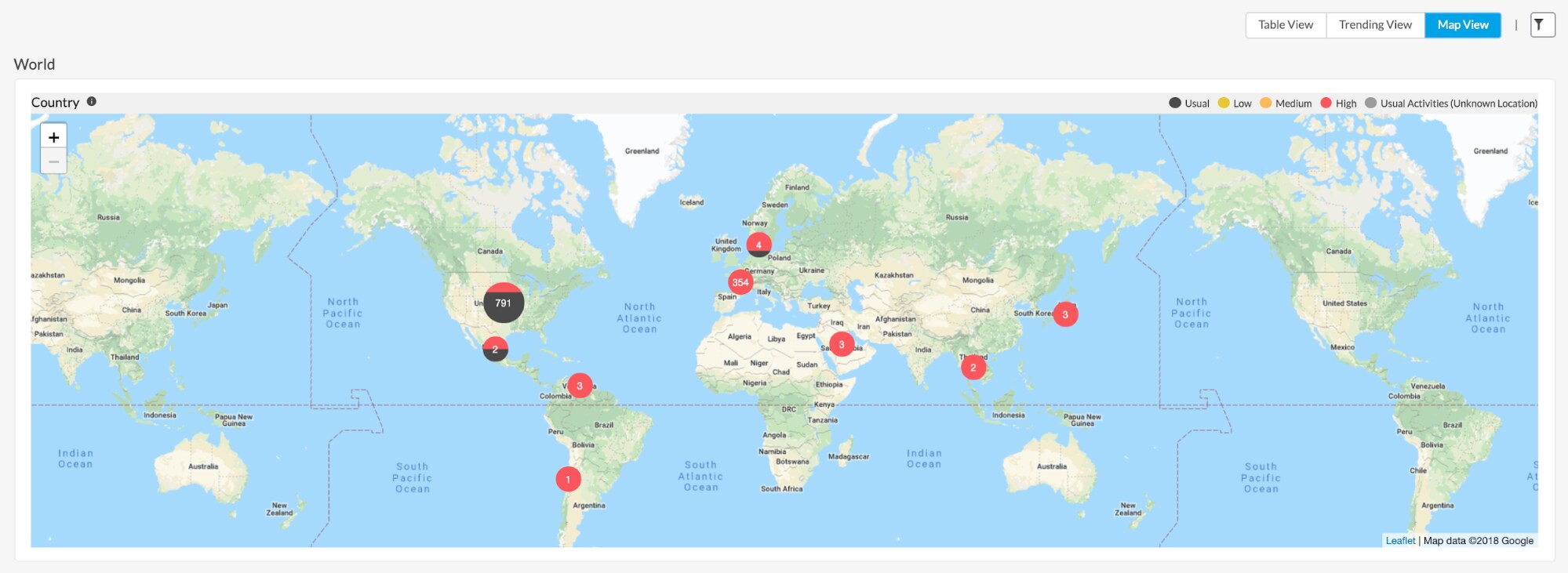
Bringing it Home
Using the techniques illustrated above, a UEBA engine helps easily and autonomously detect insider threats and user and entity account compromises. This way, you can give your security team back valuable hours in their day that they would’ve otherwise spent investigating these incidents manually.
Finally, Prisma Cloud provides a method by which admins can provide feedback to the machine learning model so it continuously learns and increases the fidelity behind the alerts. Learn more about best practices for cloud-native security.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.