The Vital Zero Trust for Private Cloud Event
Private cloud security requires a Zero Trust approach to beat back multiple threats, which are growing in virulence, volume and sophistication. Get what you need to know in our upcoming workshop Design and Deploy Zero Trust for Enterprise Private Cloud on March 29 from 10:00 AM to 12:00 PM PST. This event has been designed for you to make the most of the expertise of security visionaries and industry experts, including Founder and CTO Nir Zuk. He will walk you through practical Zero Trust architecture approaches for securing enterprise private clouds.
During this hands-on, information-packed, two-hour session, you’ll learn the essentials of meeting today’s private cloud security challenges:
- How and why Palo Alto Networks Founder and CTO Nir Zuk envisions the need for applying a Zero Trust architecture for your private cloud’s digital transformation journey.
- The application of Zero Trust best practices using virtual NGFWs in your own virtual datacenter through meaningful, hands-on labs.
- How to assemble needed tools for protecting enterprise applications and users against malware, ransomware and exfiltration.
- Ways to leverage the essential components of a complete Zero Trust network security platform.
The Shifting Perimeter Can Spell Big Trouble
For many organizations, the event can’t happen soon enough. The unique and growing challenges of private cloud security move frighteningly fast, and the time to secure your core business applications, users and devices is now.
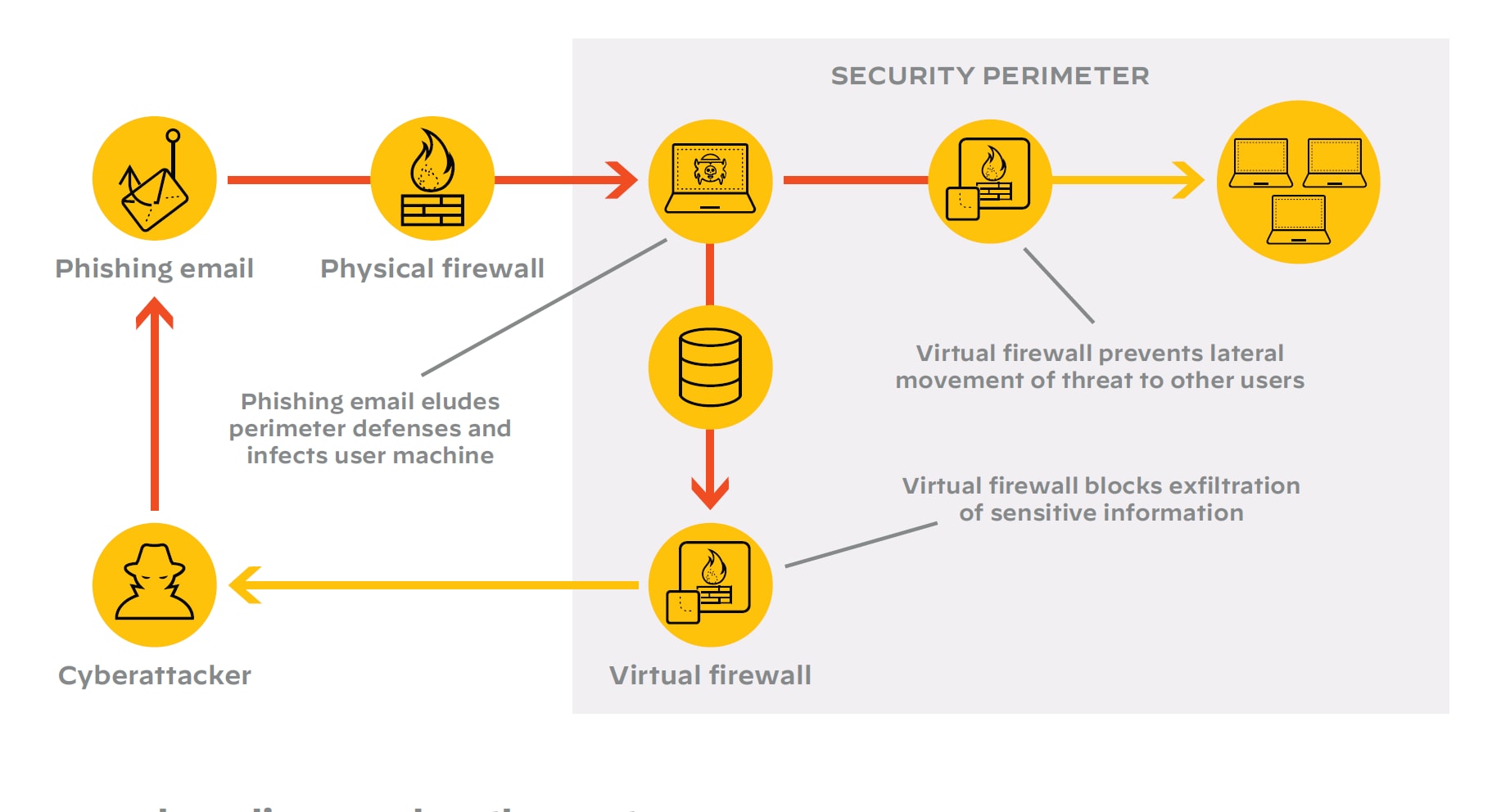
Consider this. In the time it takes you to read this blog, malware can begin to encrypt your data the instant it gains entry into your network. In the few moments it takes you to complete a simple routine work task – responding to email, having a cup of coffee, preparing for a Zoom meeting – things can go sideways fast. In a recent Palo Alto Networks Unit 42 internal study, an advanced threat replicated itself, creating more than 45,000 instances in 30 minutes across an enterprise network. Imagine the risk to your critical enterprise applications and sensitive business data!
As you’ll discover at the event, enterprises now must deal with the changing perimeter, which blurs the once-familiar concept of inside and outside. Users, applications and devices can be simply anywhere and dynamically reconfigured at cloud speed. To compound this issue, enterprises now face other threats:
- An Expanding Attack Surface – The at-home and mobile-work trend creates more and more possible entry points to attack the private cloud.
- More Sophisticated Threats – They evade security systems with techniques such as morphing into variants and encrypting traffic between the malware and the external attacker.
- Shorter Action Windows – Threats continue to get better at avoiding defenses and damaging data, applications, workloads and productivity much faster than in the past.
Integrated business applications that are inside private clouds strain legacy security solutions and discrete point products. These are not flexible or powerful enough to meet the challenges of today's real-world internal and external application integrations. External application integration, of course, can gouge gaping holes in private cloud perimeters. And, internal integrations create expanding lateral network paths, which can accelerate malware spread across your business infrastructure.
Sign Up to Isolate Your Private Cloud From Threats, and Maintain Operational Capability
We’ve organized this event to help organizations stand firm as cyber dangers threaten to erode traditional perimeters. That’s why the hands-on portion of the event has been designed to help you get started protecting core applications and sensitive data with Zero Trust enterprise architecture principles, including creating and overseeing smaller perimeters.
You’ll see why Zero Trust turns the traditional perimeter, network segments, and modern container boundaries on their heads by shifting the emphasis from implied trust to Zero Trust and allows you to take the protection of your critical data, applications, assets and services to a whole new level of security innovation.
So get ready for this event, its insights and its hands-on training. You’ll get a head start on beating back growing private cloud threats. You can also prepare for your attendance with this in-depth eBook, Five Key Challenges in Private Cloud Security, which will provide you with even more background about the essentials of a Network Security Platform vital for private cloud security.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.