Combining Carrier-Grade Private Networks with Enterprise-Grade 5G Security
As business becomes increasingly mobile, embracing 5G for private networks, edge computing and other use cases, there is a perception that network security for 5G has already been addressed by the standards that define it. While 3GPP has done excellent work to secure the numerous interfaces used for communication within a 5G core, there are still steps that can be taken to further secure the entire mobile network, including the packet core, the subscribers and the devices. You can’t secure what you can’t see, so Layer 7 mobile data inspection with next-generation threat intelligence across the user plane is critical. Palo Alto Networks has collaborated with Athonet to deploy packet cores with carrier-grade reliability, integrated with a next-generation firewall (NGFW) for enterprise-grade 5G security. This integration enables advanced security features necessary for a Zero Trust security posture for both the packet core network functions and the mobile subscribers using those functions while also providing an enterprise-focused private cellular platform offering carrier-grade performance and reliability.
Compared to non-cellular networks, private cellular is a big change from a security perspective. As access and identification is based on physical SIM cards, it provides a level of physical identity and segregation that Wi-Fi, Bluetooth and similar technologies do not provide natively. More work is needed to ensure the user plane traffic is also free from malicious traffic. For example, steps must be taken to ensure that IoT devices are not infected with malware; that key sensors on the factory floor are not exploited; and that each and every application on the private networks is known. With 5G and the various new use cases it unlocks, visibility into applications and threats will be a requirement.
To realize meaningful security in private networks, a Zero Trust security posture should be implemented. This blog won’t go into much detail on Zero Trust, so you can read more here. In short, to offer a Zero Trust security posture, you must eliminate implicit trust and answer the following questions below for each flow, as defined by the Kipling Method:
- Who should be accessing a resource? This defines the asserted (e.g., 5G) identity.
- What application is the asserted identity of the packet using to access a resource inside the protect surface?
- When is the asserted identity trying to access the resource?
- Where is the packet destination?
- Why is this packet trying to access this resource within the protect surface? This relates to data classification, where metadata automatically ingested from data classification tools helps make your policy more granular.
- How is the asserted identity of a packet accessing the protect surface via a specific application?
For a 5G network, the “Who” can be thought of as the Subscriber and Equipment identifiers. The Subscriber ID in a 5G network is the Subscriber Permanent ID (SUPI). The Equipment ID is the Permanent Equipment ID (PEI). When you have visibility into these identifiers, an enterprise leveraging 5G wireless access can quickly identify which device is infected, as well as create granular security policies that are device and subscriber aware.
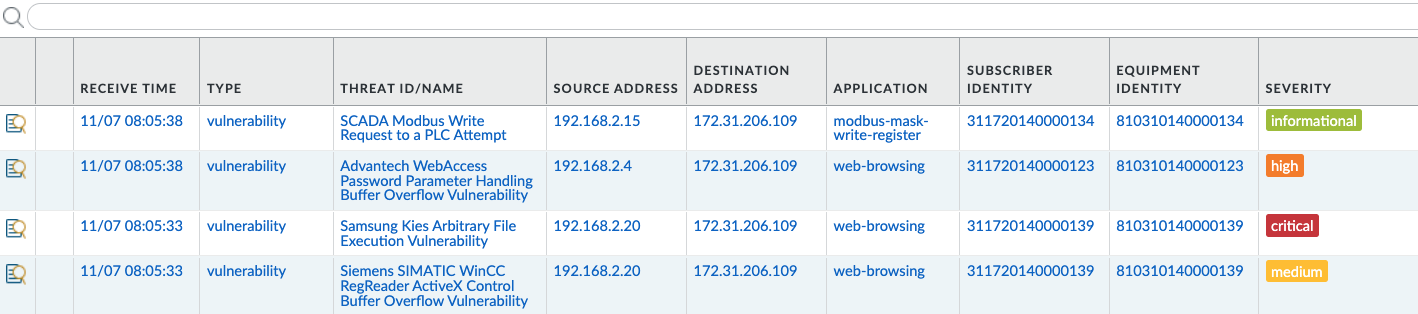
Together, Athonet and Palo Alto Networks bring to enterprises a proven mobile core network platform, coupled with the leader in enterprise security. Complete visibility is now available for all applications, across all protocols, as well as the potential threats that may be present in that traffic.
Athonet is unique in providing an enterprise-focused private cellular platform without compromising on carrier-grade performance and reliability. Palo Alto Networks is unique in its enterprise-grade 5G native security offering for both the enterprise and operators. Together, these two solutions allow enterprises to deploy private networks with the confidence that their network is carrier-grade and the security is uncompromising.
Related Blogs
Subscribe to Network Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.