Data breaches in public cloud environments continue to be a significant problem. Studies show that there were 3,950 confirmed data breaches in 2020 alone. This is partially due to the fact that detecting an exfiltration attempt is extremely challenging – it takes an average of 228 days to identify a data breach. Worse still, the average cost of a breach last year was over $3.8 million, not to mention the costs of reputational damage.
To help reduce these risks, Prisma Cloud can now analyze a combination of network flow logs and user behavior to help identify potential malicious data exfiltration attempts before they become an issue.
What Is Data Exfiltration?
Data exfiltration is when malicious actors gain access cloud environments and illegally download (steal) data.
The MITRE ATT&CK™ for Cloud framework identifies this as an "exfiltration" tactic following "initial access." Unlike other tactics in the matrix that deal with mitigating vulnerabilities, exfiltration refers to the impact after your cloud infrastructure has been compromised. It is separate from techniques for discovering vulnerabilities, as attackers have already gathered enough information to compromise an account and begin transferring data out of a cloud environment.
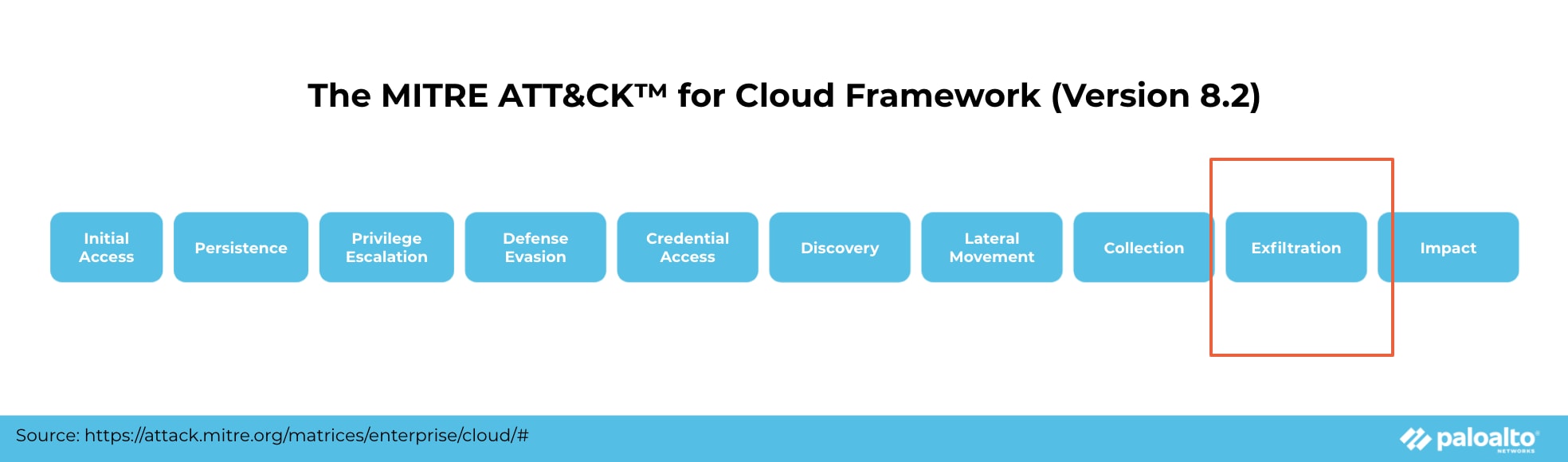
No matter the industry or size of your organization, if you have valuable data like intellectual property, financial information or personally identifiable information (PII), you are a potential target for data exfiltration. In fact, a survey conducted in 2020 shows that nearly 80% of organizations have weathered cloud security breaches.
Unfortunately, while many enterprise security teams focus on the early tactics of the ATT&CK framework to prevent attackers from infiltrating their network, most tend to overlook the signs of data leaving their network.
This is where the new network-based data exfiltration detection helps complete our customers’ security strategy.
How Does Network-Based Data Exfiltration Detection Work?
Once an attacker is able to access cloud data, the goal is to transmit as much as they can out of the network as quickly as possible. And to reduce their chances of being detected, attackers will often use a predetermined protocol, such as Hypertext Transfer Protocol (HTTP), Hypertext Transfer Protocol Secure (HTTPS), Domain Name System (DNS) or File Transfer Protocol (FTP), to transmit the data.
However, these activities would almost certainly deviate from normal user behavior patterns. For example, the data volume may be much greater than most users would transmit. They may also be accessing the environments from a known TOR exit node.
Knowing this, Prisma Cloud uses advanced machine learning (ML) algorithms to analyze network flow logs and user behaviors to create a model of baseline activity. It can then detect deviations from that baseline that could signal malicious data exfiltration attempts, and create an alert.
Network Anomaly Detection in Prisma Cloud
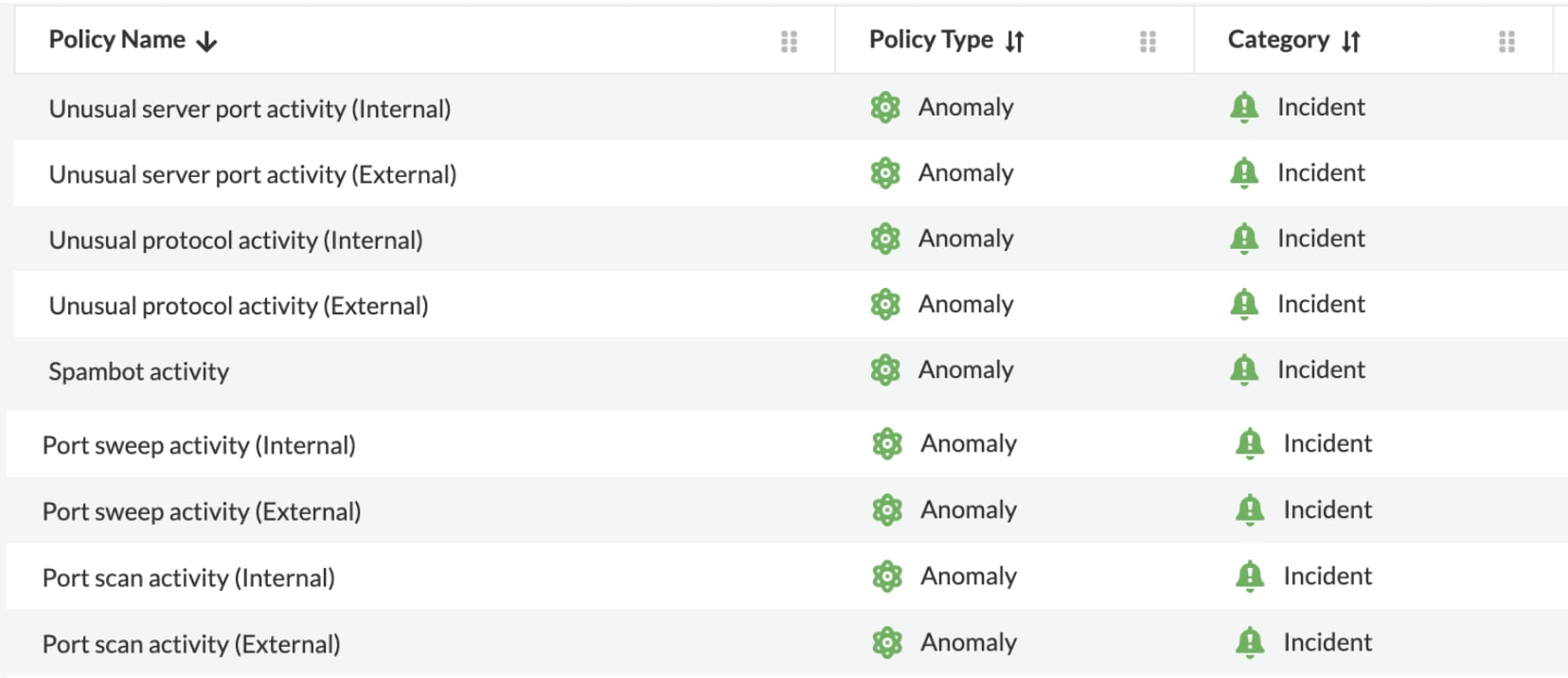
Beyond data exfiltration monitoring, Prisma Cloud provides a rich set of ML-based detection capabilities for anomalous network activities like:
Port Scan Activity
Identifies port scan attempts by inspecting inbound and outbound network traffic. It refers to the "discovery" tactic defined in the ATT&CK framework for cloud.
Spambot Activity
Identifies if a host inside the customer's cloud environment is generating outbound SMTP traffic and for which no prior mail-related network activity has been observed. It refers to the "impact" tactic in the ATT&CK framework.
Unusual Protocol Activity
Identifies network activity from a client host to a server host inside the customer's cloud environment, using an unknown IP protocol. It refers to the "defense evasion" tactic in the ATT&CK framework.
Together, these capabilities allow users to continuously monitor flow logs generated from network traffic in each environment and look for any potential malicious activity.
Next Steps
Network-based data exfiltration detection will be available to Prisma Cloud users in the next two months. To learn more about how to operationalize Cloud Security Posture Management (CSPM) in the meantime, check out our white paper, Guide to CSPM Tools.