Start Building Your Zero Trust Architecture with ZTNA 2.0
This post is also available in: 日本語 (Japanese)
According to our recent What’s Next in Cyber: A Global Executive Pulse Check global survey, 47% of survey respondents noted that maintaining a secure hybrid workforce is one of their top reasons for adopting a zero trust architecture (ZTA). However, 98% of CXOs admitted in this same survey that they find Zero Trust implementation challenging for three main reasons:
- Not knowing where to start and how to prioritize
- Lack of qualified vendors with a complete and integrated solution
- Lack of internal expertise
Good news—we can help you with all three of these things. Let’s start from the beginning: where should you start your ZTA adoption? Start with ZTNA 2.0.
Why ZTNA 2.0 is Your ZTA Starting Point
You may have a few thoughts running through your mind right now, like “What is ZTNA 2.0? We haven’t even started with ZTNA 1.0. Do we need to ZTNA 1.0 first? What even is ZTNA? Why are there version numbers?”
Here is a quick, three-point primer to address these questions and get us all acclimated.
- What is ZTNA? ZTNA is the acronym for Zero Trust Network Access. It is a category of technologies that provides secure remote access to applications and services based on strict access control policies that treat all users and devices as untrusted until proven otherwise.
- What is ZTNA 1.0? ZTNA 1.0 is shorthand for legacy ZTNA approaches. ZTNA 1.0 supports only coarse-grained access controls, incorporates an “allow and ignore” approach for both users and app traffic, and provides either little or no advanced security consistently across all apps and data. These shortcomings violate the principle of least privilege and increase organizational security breach exposure.
- What is ZTNA 2.0? ZTNA 2.0 is the most cutting-edge approach to ZTNA, overcoming ZTNA 1.0 limitations to deliver the comprehensive cybersecurity benefits envisioned with ZTA.
When you start building out your ZTA with ZTNA 2.0, you harness five powerful principles to protect your users, data, apps, and devices. These five principles are:
- Least-privileged access. Enables precise access control at the application and sub-application levels, independent of network constructs such as IP addresses and port numbers.
- Continuous trust verification. After access is granted to an application, continuous trust assessment continues based on changes in device posture, user behavior, and application behavior.
- Continuous security inspection. Uses deep, continuous inspection of all application traffic, including for allowed connections, to help prevent threats, including zero-day threats.
- Protection of all data. Provides consistent control of data across all applications, including private applications and SaaS applications, with a single data loss prevention (DLP) policy.
- Security for all applications. Consistently protects all types of applications in use across the enterprise, including modern cloud-native applications, private legacy applications, and SaaS applications.
ZTNA 2.0 Secures Your Hybrid Workforce in a Perimeter-Less World
ZTNA 2.0 is imperative to help address one of the biggest security challenges today: the perimeter-less nature of modern networks. With the hybrid workforce’s widespread use of cloud-based applications, mobile devices, and the internet of things (IoT), it’s becoming increasingly difficult for network security professionals to define and protect their organization’s “perimeter.” This perimeter-less world makes it harder to control access to sensitive data and systems, leaving organizations more vulnerable to attacks from both external and internal actors.
ZTNA 2.0 doesn’t adhere to a perimeter-based construct for secure access. Instead, it consistently verifies and authenticates every user, device, application, and data before granting access to the network, regardless of whether these elements are inside or outside the organization's physical boundaries. This location-agnostic verification and authentication available with ZTNA 2.0 make it more difficult for an attacker to move laterally through the network and helps reduce the attack surface.
Start at ZTNA 2.0![Prisma Access delivers ZTNA 2.0.]()
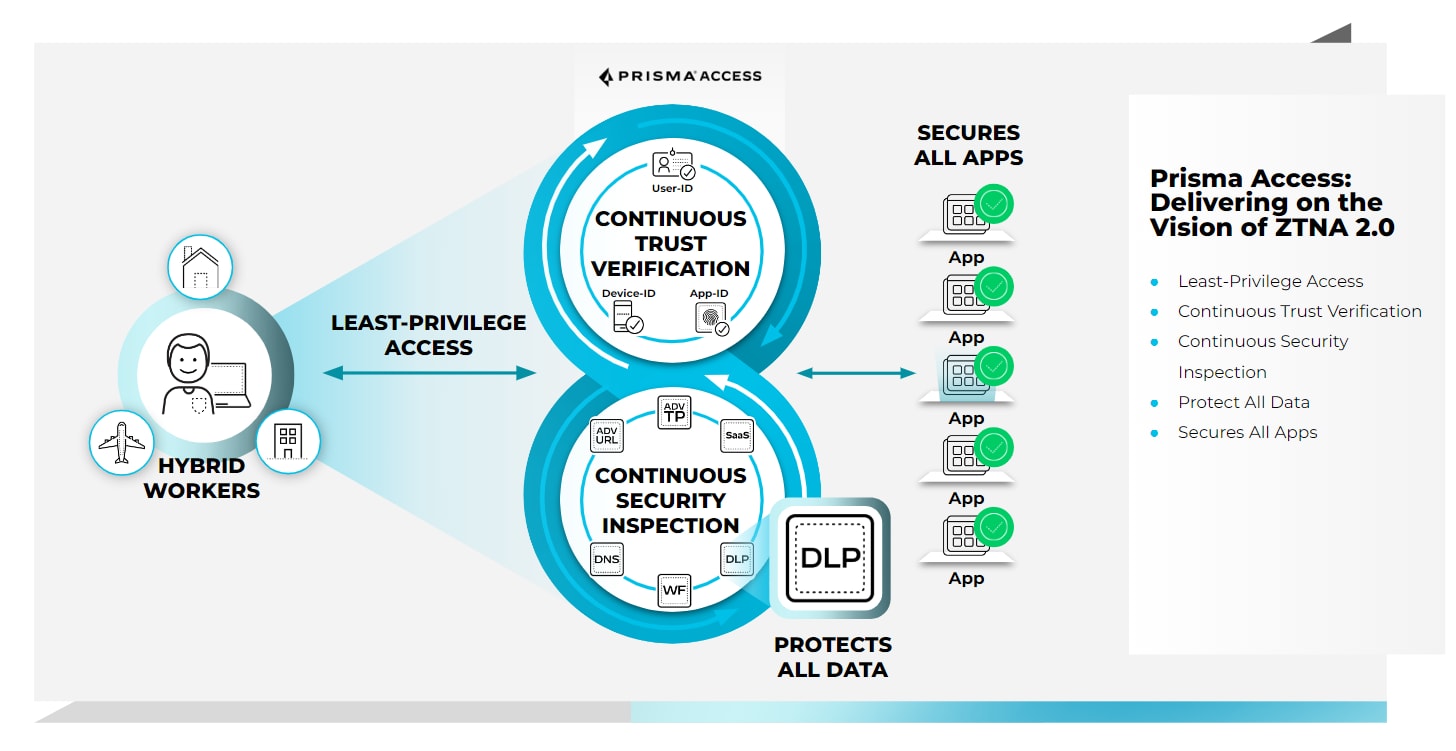
ZTA is a remarkably useful cybersecurity architecture to help you keep your organization protected in a world where work is an activity, not a place. Start building your ZTA strategy with ZTNA 2.0, the new standard for providing secure access for all of your users, devices, applications, and data.
If you’d like to talk to someone about how ZTNA 2.0 can help your organization, please reach out. We are excited and ready to help you start planning and implementing your ZTA strategy.
Related Blogs
Subscribe to Sase Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.