We don’t just recommend ZTNA 2.0. We also use it.
This post is also available in: 日本語 (Japanese)
The last few years have changed how and where many people work, redefining the concept of work from a place we go to an activity we perform. This is why we’ve delivered Zero Trust Network Access (ZTNA) 2.0: so that every employee can access the data and applications they need on any device they choose, wherever they work — all while still meeting strict security requirements.
We built a security solution to match how people work today, with an eye to the future
At the height of the pandemic, many businesses focused on trying to scale their existing virtual private network (VPN) infrastructures to connect their newly enabled remote workers to the resources they needed. Companies quickly realized VPN was not built to scale secure connections for an almost fully remote workforce.
Some organizations think VPNs may be the answer as they activate return-to-office (RTO) plans. Even with RTO, though, there are still too many employees outside the office perimeter at any given time to have VPNs be a workable solution for providing employees with high-performance access to the corporate apps and services they need to get their jobs done.
In addition to the employees working outside the corporate perimeter, businesses also have critical applications and data hosted outside company walls—including internet-based and Software-as-a-Service (SaaS) apps—that require protection and secure access.
Our needs are the same as everyone else's: secure access to data and applications, anywhere, on any device
We here at Palo Alto Networks are wrestling with the same challenges as other companies. We have a large, dispersed remote employee contingent and concentrated employee populations around our Santa Clara headquarters and various worldwide offices. We use a combination of cloud-based, internally-hosted, and homegrown applications and services for day-to-day productivity and mission-critical business processes.
ZTNA 2.0 is the right architecture to support our employees wherever they work, providing a secure, fast, and frictionless experience whether they work from home, in the office, or from the corner café—sometimes all on the same day. And we make sure they can securely access the data and applications they need to do their jobs, whether these resources are in the cloud or within our own datacenters.
What ZTNA 2.0 looks like at Palo Alto Networks
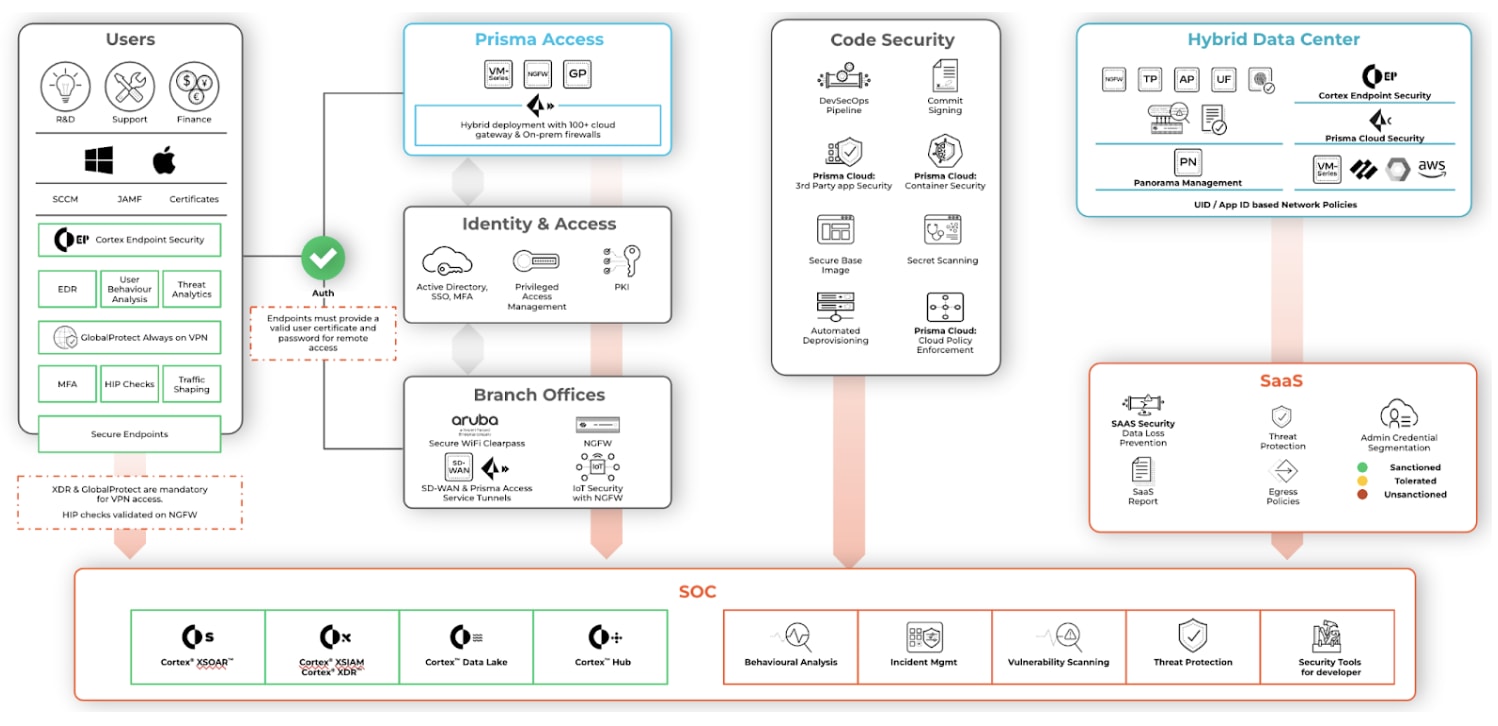
We use Prisma Access to secure our hybrid workforce. Security in a hybrid environment needs continuous trust verification along with continuous traffic inspection for all apps and all data to ensure protection from data leaks, exploit attempts, and malware. We also need to track user behavior, including identity and privilege level management.
The Palo Alto Networks ZTNA 2.0 implementation
ZTNA 2.0 delivered with Prisma Access gives us exactly this capability. Our IT team has shared a thorough explanation of how we’ve deployed Prisma Access and use ZTNA 2.0 in the context of five key lifecycle principles:
- Least-privileged access. Enables precise access control at the application and sub-application levels, independent of network constructs such as IP addresses and port numbers.
- Continuous trust verification. After access is granted to an application, continuous trust assessment continues based on changes in device posture, user behavior, and application behavior.
- Continuous security inspection. Uses deep, continuous inspection of all application traffic, including for allowed connections, to help prevent threats, including zero-day threats.
- Protection of all data. Provides consistent control of data across all applications, including private applications and SaaS applications, with a single data loss prevention (DLP) policy.
- Security for all applications. Consistently protects all types of applications in use across the enterprise, including modern cloud-native applications, private legacy applications, and SaaS applications.
ZTNA 2.0 is the more secure way forward for us. It can be for you, too.
We don’t just think you should use ZTNA 2.0; we use it, too. With ZTNA 2.0, all of us can better meet our organizational compliance and security requirements without sacrificing productivity or efficiency. Check out our website to get even more details on how ZTNA 2.0 works and can help solve your security challenges.
Related Blogs
Subscribe to Sase Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.